
Code corre un editor de codigo Python donde realizamos bypass a un filtro para la ejecucion de comandos y obtener acceso a la maquina. Tras la lectura de hashes en la base de datos SQLite accedimos por el servicio SSH. Finalmente escalamos privilegios tras modificar el archivo de configuracion para la creacion de backups de backy logrando leer y acceder a archivos como root y posteriormente acceso por SSH.
| Nombre | Code |
|---|---|
| OS | Linux |
| Puntos | 20 |
| Dificultad | Easy |
| Fecha de Salida | 2025-03-22 |
| IP | None |
| Maker | |
|
Recon
nmap
nmap muestra multiples puertos abiertos: http (5000) y ssh (22).
|
|
Web Site
El sitio web en el puerto 5000 muestra gunicorn como servidor.
|
|
Al visitar el sitio muestra un editor de codigo donde se muestran dos ‘ventanas’, para ejecucion y salida.
Se indica que el editor es para lenguaje Python.
Tambien se muestra formularios de Registro y Login.
Al registrar un usuario y autenticarse, muestra la opcion ‘My codes’ donde es posible acceder a “archivos” de codigo guardados por el usuario.
Python - Code Execution
Tras intentar ejecutar comandos mediante librerias Python se indica la existencia de un filtro.
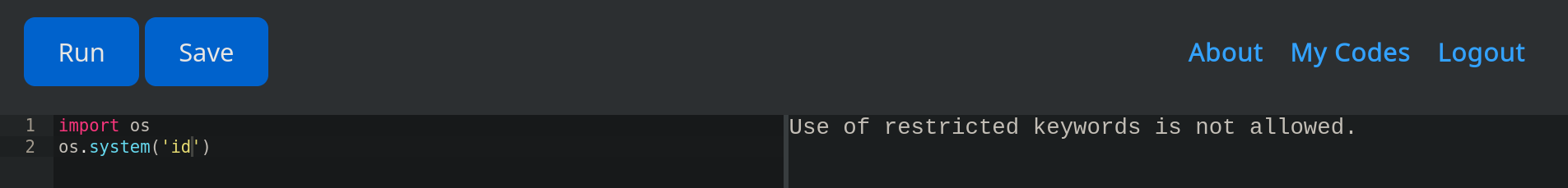
Intentamos realizar la ejecucion con varias librerias y payloads para realizar bypass al filtro, encontramos que las siguientes “palabras” no son aceptadas.
|
|
Exploramos globals() el cual muestra las diferentes variables, funciones y clases definidas dentro del codigo.
|
|
Observamos que se esta utilizando Flask y una lista de clases y funciones. Entre las funciones se muestra render_template_string, una base de datos sqlite en /home/app-production/app/instance/database.db tambien la clase User.
|
|
Command Execution
render_template_string
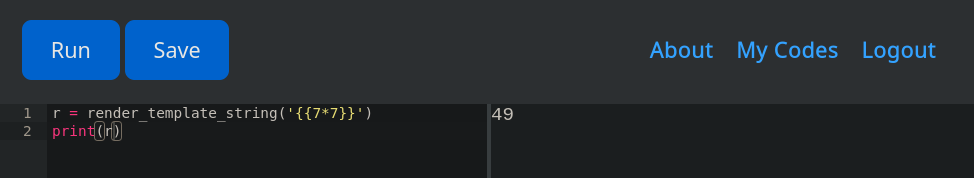
Es posible utilizar render_template_string, se muestra la ejecucion de {{7*7}}.
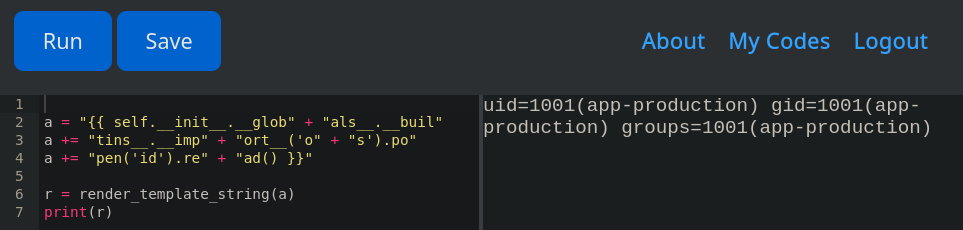
Ejecutamos el comando id con os concatenando el payload para realizar “bypass”. Se muestra el resultado.
globals + getattr
Basados en globals() es posible ejecutar codigo junto con getattr().
|
|
Se observa una solicitud desde la maquina.
|
|
AI Payload
Asi tambien, basados con las palabras no aceptadas ChatGPT nos muestra un payload mas “complejo”.
|
|
User - app-production
Ejecutamos una shell inversa utilizando shells, obteniendo una shell como app-production y la flag user.txt.
|
|
Encontramos el codigofuente de la aplicacion en app/app.py se observa que render_template_string no esta siendo utilizando dentro del codigo. Ademas vemos multiples palabras como filtro en la ruta run_code.
Database
Encontramos la base de datos sqlite de la aplicacion.
|
|
Transferimos esta a nuestra maquina.
|
|
Observamos unicamente dos usuarios y el hash de cada uno.
|
|
crackstation muestra en texto plano el valor de los hashes.
| Hash | Type | Result |
|---|---|---|
| 759b74ce43947f5f4c91aeddc3e5bad3 | md5 | development |
| 3de6f30c4a09c27fc71932bfc68474be | md5 | nafeelswordsmaster |
User - Martin (1)
Observamos que martin esta registrado en la maquina.
|
|
Utilizamos la contrasena por el servicio SSH logrando el acceso a este usuario.
|
|
User - Martin (2)
Es posible obtener la contrasena de Martin obteniendo el hash de la base de datos desde el editor de codigo.
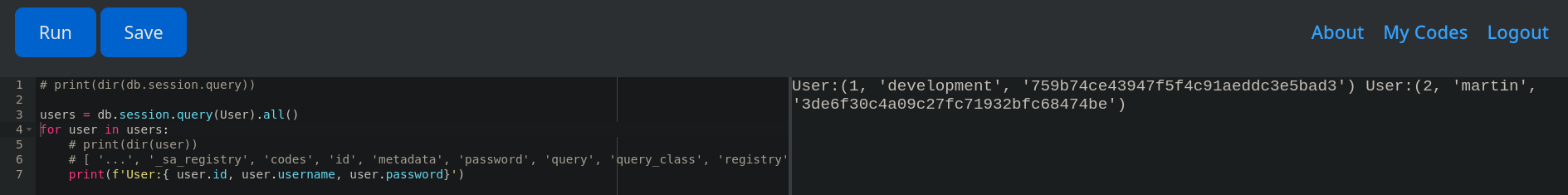
Privesc
Vemos que es posible ejecutar como root el script backy.sh.
|
|
El script acepta un archivo .json, dentro del archivo busca por los directorios /var/ y /home en 'directories_to_archive', de no exisitir se cierra, en caso contrario pasa el archivo al comando backy.
|
|
Dentro del directorio de martin encontramo sun ejemplo de archivo json, asi como un backup.
|
|
El backup muestra el codigo de la aplicacion web.
|
|
Tras ejecutar el script con el archivo json observamos que crea un backup del directorio especificado en directories_to_archive.
|
|
Backup /root/
Modificamos el archivo json eliminando exclude y apuntando al directorio /root/.
|
|
Ejecutamos el script con el archivo json.
|
|
Observamos que se creo el archivo backup.
|
|
Tras extraer los archivos del backup observamos la flag root.txt y la clave privada SSH de root.
|
|
Shell
Utilizamos la clave privada en SSH localmente logrando acceder como root.
|
|
Dump Hashes
Realizamos la lectura del archivo /etc/shadow.
|
|
